Table of Contents
Top 7 Cybersecurity Threats to Prepare For in 2023 (Cybersecurity Infographics)
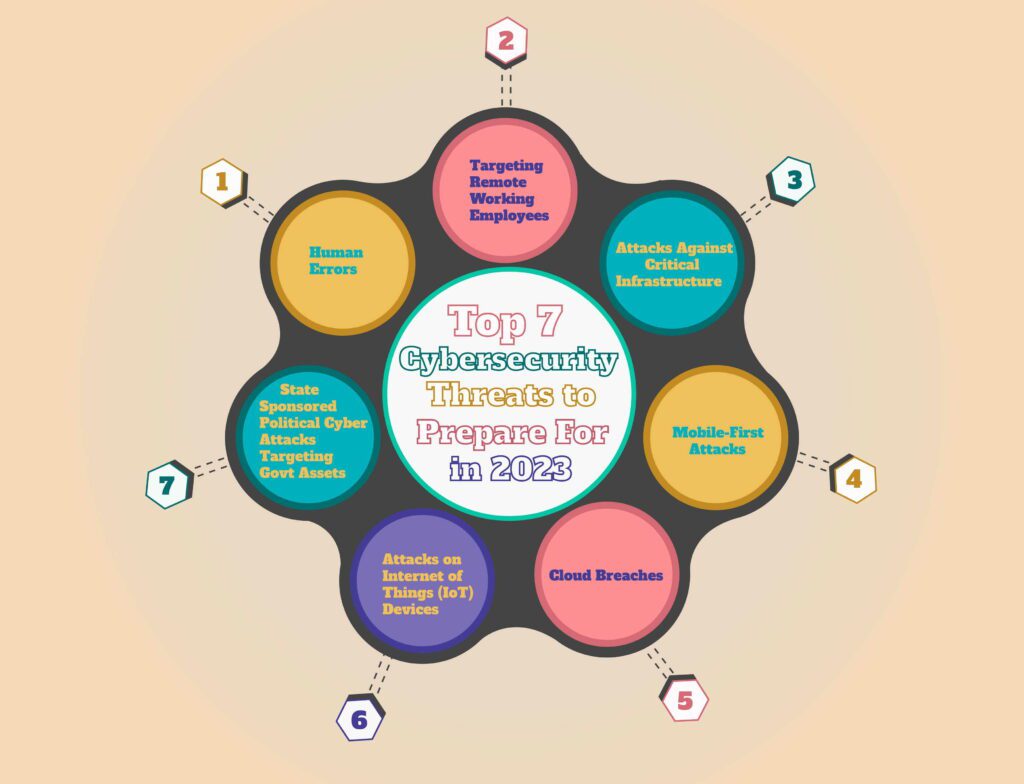
1. Human Errors
2. Targeting Remote Working Employees
3. Attacks Against Critical Infrastructure
4. Mobile-First Attacks
5. Cloud Breaches
6. Attacks on Internet of Things (IoT) Devices
7. State Sponsored Political Cyber Attacks Targeting Govt Assets
Top 7 Attacks Your Organization Should Watch Out for in 2023 (Cybersecurity Infographics)

1) Multi-Factor Authentication (MFA) Attack
2) Hardware and Software Vulnerabilities
3) Shadow APIs
4) Attacks through Mobile Devices
5) The Digital Supply-Chain Assault
6) Ransomware
7) Persistent Phishing
Cybersecurity Market Statistics (Infographics)

- The cybersecurity market is expected to grow to $300 billion by 2024.
- Global spending on cybersecurity exceeded $1 trillion in 2021.
- On average, small businesses spend less than $500 on cybersecurity.
- Microsoft invests $1 billion annually on cybersecurity.
- JPMorgan Chase spends $600 million on cybersecurity every year.
- The US government’s 2019 budget for cybersecurity is $15 billion.
- Every third US company has purchased data-breach insurance coverage or cyber liability insurance.
- The cyber insurance market is expected to be worth $20 billion by 2025.
- Companies pay up to $500,000 for hackers to test their systems.
The 10 Biggest Ransomware Attacks of 2021 (Infographic)
Below is the list of high profile Ransomware attacks on firms & corporations (Compilation Source: Touro College)
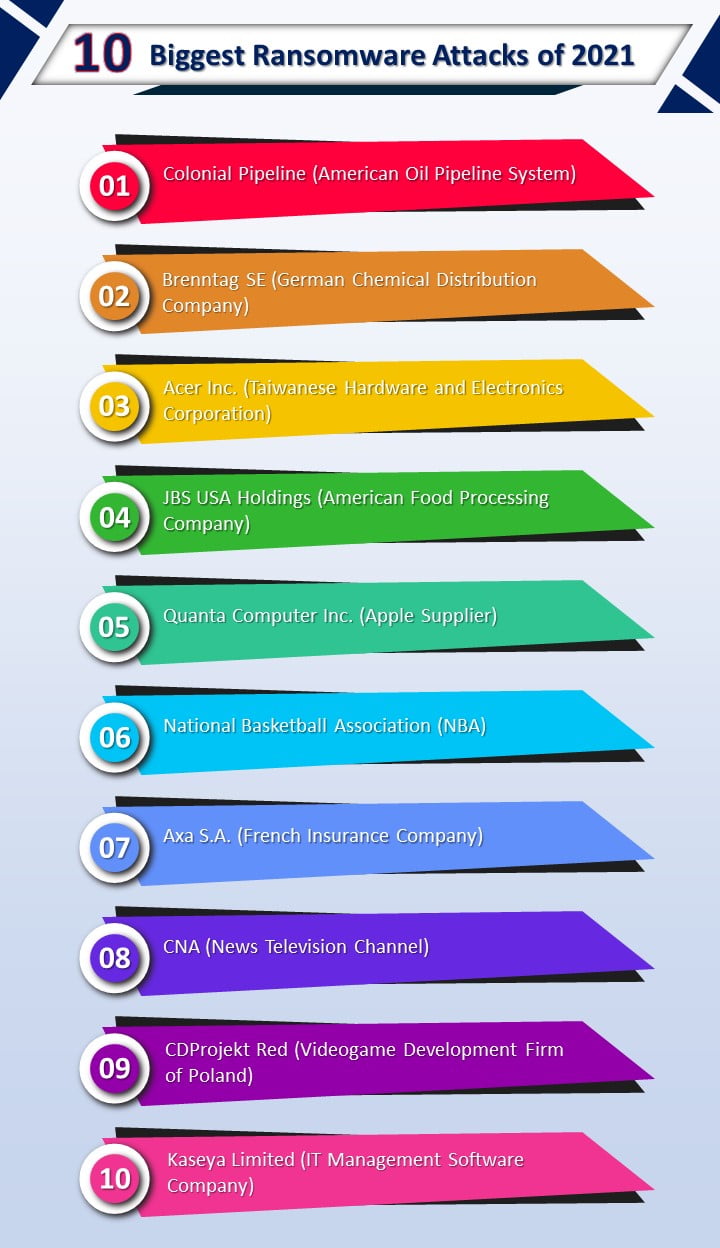
- Colonial Pipeline (American Oil Pipeline System)
- Brenntag SE (German Chemical Distribution Company)
- Acer Inc. (Taiwanese Hardware and Electronics Corporation)
- JBS USA Holdings (American Food Processing Company)
- Quanta Computer Inc. (Apple Supplier)
- National Basketball Association (NBA)
- Axa S.A. (French Insurance Company)
- CNA (News Television Channel)
- CDProjekt Red (Videogame Development Firm of Poland)
- Kaseya Limited (IT Management Software Company)
Top 10 Countries Targeted For Cyber Attacks in 2021 (% Wise) – Infographic

- United States: 38%
- India: 17%
- Japan: 11%
- Taiwan: 7%
- Ukraine: 6%
- South Korea: 6%
- Brunei: 4%
- Russia: 4%
- Vietnam: 4%
- Pakistan: 3%
12 Strategic Technology Trends for 2022 According To Gartner (Infographic)

According to Gartner, 12 strategic technology trends that are being adopted by businesses in 2022
- Data Fabric
- Cybersecurity Mesh
- Privacy-Enhancing Computation
- Cloud-Native Platforms
- Composable Applications
- Decision Intelligence
- Hyperautomation
- AI Engineering
- Distributed Enterprises
- Total Experience
- Autonomic Systems
- Generative AI
List of Sectors Which Suffered The Most Security Breaches (% Wise) – Infographic
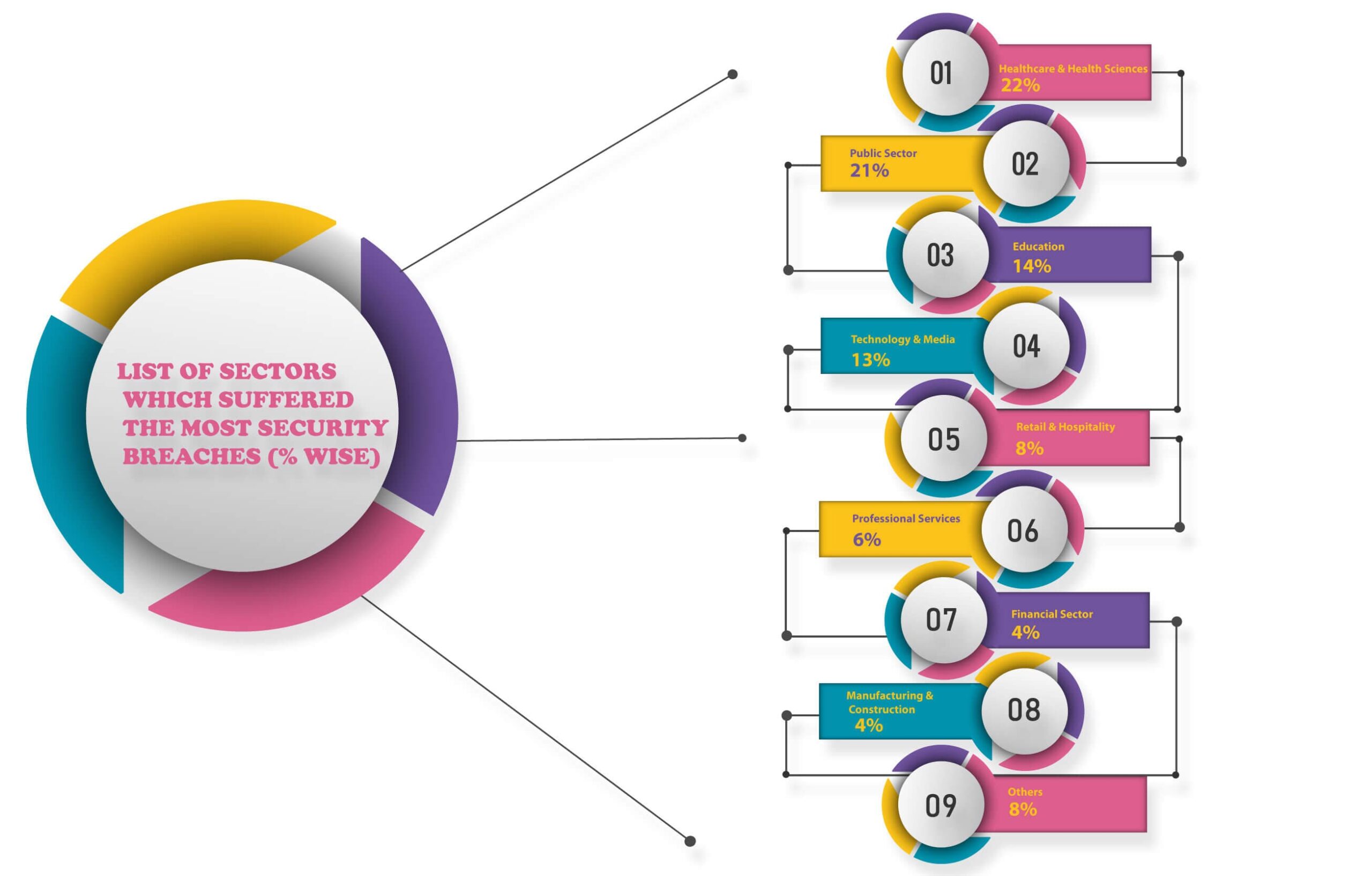
- Healthcare & Health Sciences – 22%
- Public Sector – 21%
- Education – 14%
- Technology & Media – 13%
- Retail & Hospitality – 8%
- Professional Services – 6%
- Financial Sector – 4%
- Manufacturing & Construction – 4%
- Others – 8%
Biggest Data Breaches of Organizations Reported in 2021 (Infographic)

- Microsoft Exchange Servers have been attacked with 0-day exploits by Hafnium, a state-sponsored group operating out of China. (AP News)
- Personal data of 533 million Facebook users in 106 countries have been leaked online. (Business Insider)
- Hackers scrapped the data of 700 million Linkedin users and have put it up for sale online. (Fortune)
- A vehicle for hire App called Bykea accidentally exposed 400 million records of its customer’s data on the production server. (SafetyDetectives)
- 220 million Brazilian citizens’ data was hacked by Lapsus$ Group from the official website of Brazil’s Ministry of Health. (Statista)
- Colonial Pipeline was attacked by ransomware linked to the DarkSide group which proactively took certain pipeline operations systems offline and demanded an amount of $4.4 million. (Bloomberg)
7 Top Trends in Cybersecurity For 2022 According To Gartner (Infographic)

1. Attack surface expansion
2. Identity system defense
3. Digital supply chain risk
4. Vendor consolidation
5. Cybersecurity mesh
6. Distributed decisions
7. Beyond awareness
10 Cybersecurity Predictions For 2022 (Infographic)

1. User Awareness
2. Geo-Targeted Phishing Threats
3. Attacks on the Healthcare Sector
4. Machine Learning
5. Cloud Security
6. GDPR Compliance
7. Threats to Higher Education
8. Vulnerability of IoT
9. Mobile Devices as Attack Vectors
10. Financial Services Cyberattacks
Source: (financesonline)
Types of Network Security Attacks (Infographic)
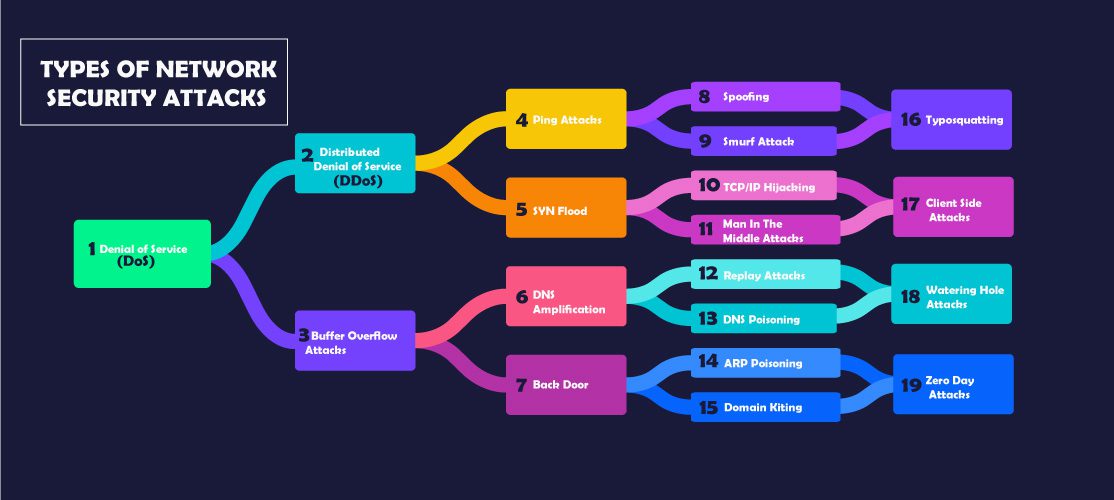
- Denial of Service (DoS)
- Distributed Denial of Service (DDoS)
- Buffer Overflow Attacks
- Ping Attacks
- SYN Flood
- DNS Amplification
- Back Door
- Spoofing
- Smurf Attack
- TCP/IP Hijacking
- Man In The Middle Attacks
- Replay Attacks
- DNS Poisoning
- ARP Poisoning
- Domain Kiting
- Typosquatting
- Client Side Attacks
- Watering Hole Attacks
- Zero Day Attacks
Top 10 Ransomware Attacks By Revenue in 2021 (Infographic)

1. Conti – $175 million
2. DarkSide – $80 million
3. Phoenix Cryptolocker – $55 million
4. REvil/Sodinokibi – $35 million
5. Cuba – $17 million
6. Clop – $16 million
7. LockBit – $15 million
8. Hive – $15 million
9. BlackMatter -$14 million
10. Ryuk – $13 million
Historical Hacking Statistics (Infographic)

- Security breaches have increased by 64% since 2014 and 11% since 2018. (Accenture)
- In the event of a security breach, 56% of Americans don’t know what steps to take. (Varonis)
- In 2020, personal data was involved in 58% of all security breaches. (Verizon)
- The average time to identify a security breach was 207 days in the year 2020. (IBM)
- From identification to containment, the average lifecycle of a breach was 280 days till 2020. (IBM)
- 64% of Americans have never bothered to check if they were affected by a data breach. (Varonis)
- In 2020, the average cost of a data breach is $3.86 million. (IBM)
Statistics For The Cost of Cyber Crime (Infographic)

- Cybercrimes see a 600% increase and this increase was found during the covid 19 pandemic
- Experts estimate that by the year 2025, around $ 10.5 trillion will be spent annually on cybercrimes all over the world.
- The global annual cost of cybersecurity crime is estimated to be approximately $6 trillion per year.
- The cost of cybercrime makes up 1% of the global GDP.
- Did you know that on average, a malware attack costs any company more than $2.5 million (including the time cost required to troubleshoot the attack.
- Do you know that ransomware is about 57 times more destructive and dangerous in the year 2021 than in the year 2015?
- There are a total of 30 million SMBs in the United States and more than 66% of all SMBs have had at least 1 incident between 2018-2020.
- Did you know that the average cost of a data breach for a small business or company can range from approximately $120,000 to $1.24 million.
- The total cost of a data breach increased from $3.86 million to $4.24 million in 2021, the highest average total cost in the report’s 17-year history.
- The average cost of breaches increased by $1.07 million with remote work being a significant contributing factor to the breach.
- Security-driven AI had the finest cost mitigation, saving up to $3.81 million (80% cost variance).
- Did you know that zero trust protection policies have saved up to $1.76 million per breach?
- It costs $180 per record with a violation of PII.
- Among all types of cyber-attacks, the largest number of attacks are carried out on SMBs with more than 50%.
- Many enterprises experienced an average of about 130 security breaches per organization per year.
- Enterprises saw a 22.7% increase in the total annual cost of cyber security in 2021.
- Did you know that the annual number of security breaches at enterprise organizations increased by about 27.4%.
- Did you know that an average company needs 50 days to solve an insider attack and 23 days to recover from a ransomware attack?
- Around 71.1 million people worldwide are victims of cyber crimes every year.
- Cybercrime causes up to $318 billion in damages to individuals.
- Persons caught in phishing scams face an average loss of $225.
- Access to a person’s entire online identity costs about $1,000.
- Did you know you can get malware + tutorials and how to use it for $50?
- A $34 monthly speculation could net the criminal $25,000 a month.
Statistics For Security Spending and Costs (Cybersecurity Infographic)
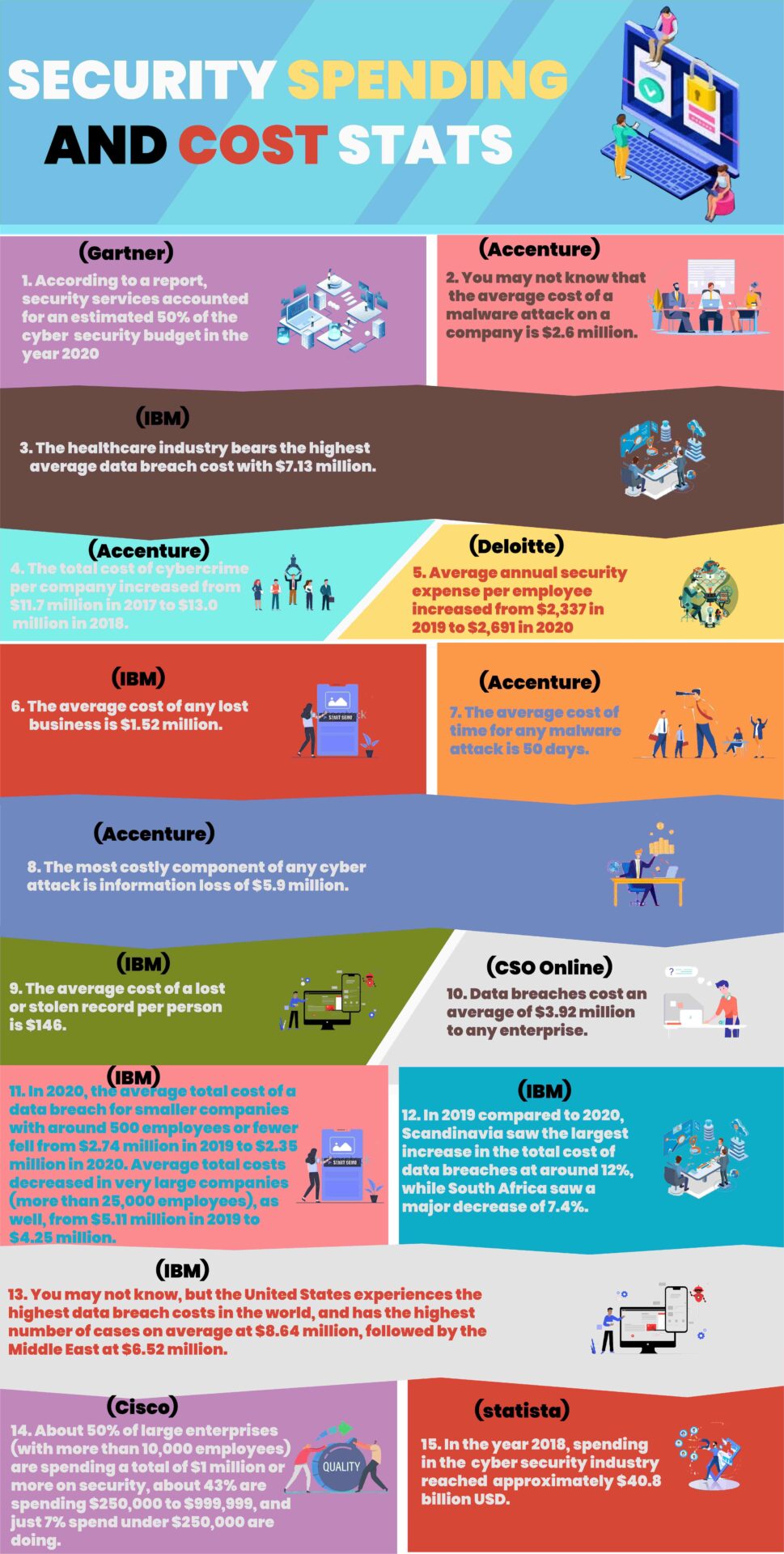
1. According to a report, security services accounted for an estimated 50% of the cyber security budget in the year 2020 (Gartner)
2. You may not know that the average cost of a malware attack on a company is $2.6 million. (Accenture)
3. The healthcare industry bears the highest average data breach cost with $7.13 million. (IBM)
4. The total cost of cybercrime per company increased from $11.7 million in 2017 to $13.0 million in 2018. (Accenture)
5. Average annual security expense per employee increased from $2,337 in 2019 to $2,691 in 2020 (Deloitte)
6. The average cost of any lost business is $1.52 million. (IBM)
7. The average cost of time for any malware attack is 50 days. (Accenture)
8. The most costly component of any cyber attack is an information loss of $5.9 million. (Accenture)
9. The average cost of a lost or stolen record per person is $146. (IBM)
10. Data breaches cost an average of $3.92 million to any enterprise. (CSO Online)
11. In 2020, the average total cost of a data breach for smaller companies with around 500 employees or fewer fell from $2.74 million in 2019 to $2.35 million in 2020. Average total costs decreased in very large companies (more than 25,000 employees), as well, from $5.11 million in 2019 to $4.25 million. (IBM)
12. In 2019 compared to 2020, Scandinavia saw the largest increase in the total cost of data breaches at around 12%, while South Africa saw a major decrease of 7.4%. (IBM)
13. You may not know, but the United States experiences the highest data breach costs in the world, and has the highest number of cases on average at $8.64 million, followed by the Middle East at $6.52 million. (IBM)
14. About 50% of large enterprises (with more than 10,000 employees) are spending a total of $1 million or more on security, about 43% are spending $250,000 to $999,999, and just 7% spend under $250,000 are doing. (Cisco)
15. In the year 2018, spending in the cyber security industry reached approximately $40.8 billion USD. (Statista)
Latest Cybersecurity Job Statistics (Infographic)

1. About 61% of companies feel that their cybersecurity applicants are not fully qualified. (ISSA)
2. Around 70% of cyber security professionals claim that their organization suffers from a lack of cyber security skills. (ESG and ISSA)
3. Since the year 2016, due to GDPR demands, the demand for Data Protection Officers (DPOs) has increased tremendously and has increased by almost 700%. (Reuters)
4. According to a report there are about 500,000 Data Protection Officers (IAAP)
5. Almost more than two-thirds of cyber security professionals are struggling to define their career path and job. (ISSA)
6. Around 61% of cyber security professionals are not completely satisfied with their current job. (ISSA)
7. There was an increase of about 350 percent in open cyber security positions from 2013 to 2021. (cybercrime magazine)
8. Nearly 40 percent of IT leaders and experts say that cybersecurity jobs are one of the toughest to fill. (CSO Online)
9. Cybersecurity experts are some of the maximum paying positions starting from an average of $140K annually. (cybint)
Covid-19 Cybersecurity Statistics (Infographic)

- It has been observed that there has been an increase of almost 300% in cyber-attacks since the start of the covid 19 pandemic, confirmed by the FBI itself (IMC GROUP)
- About 27% of COVID-19 cyber-attacks target banks or healthcare organizations and in the year 2020, the number of cyber-attacks on banks has increased to 238% and is responsible for all of them due to covid 19 (Fintech News)
- Confirmed data breaches in the healthcare industry increased by almost 58% in 2020 (Verizon)
- In May, about 33,000 unemployment applicants from the unemployment assistance program suffered a data security breach during the pandemic. (NBC)
- Americans lost approximately $97.39 million to COVID-19 and stimulus check scams. (AtlasVPN)
- During the Covid 19 pandemic in the month of April, in the year 2020, Google blocked more than 18 million daily malware and phishing emails related to coronavirus (Google)
- Nearly 52% of legal and compliance leaders are concerned about third-party cyber risks due to remote working since COVID-19. (Gartner)
- Remote work or work from home has increased the average cost of a data breach by $137,000. (IBM)
- About 47% of employees suspected a phishing scam while working from home and cited it as a cause of distraction. (Tessian)
- Around 81% of cyber security professionals have reported a change in their job function during the covid pandemic. (ISC)
- In April 2020, nearly half a million Zoom user accounts were compromised and sold on a dark web forum. (CPO Magazine)
- A report found that cloud-based cyber-attacks increased by almost 630% between January and April 2020. (Fintech News)
- Remote workers have committed a security breach in about 20% of organizations. (Malwarebytes)
GDPR Cybersecurity Statistics (Infographic)
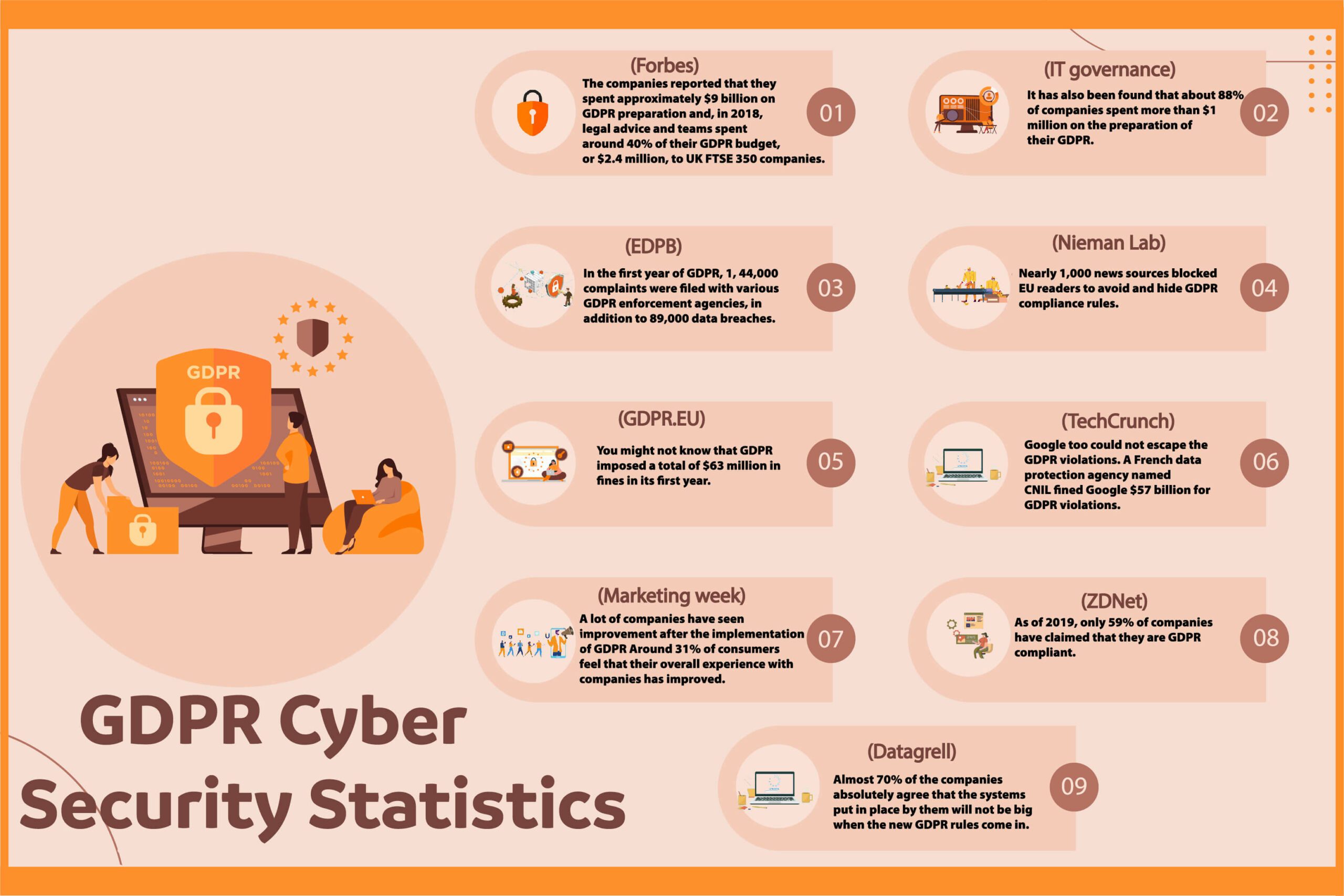
1. The companies reported that they spent approximately $9 billion on GDPR preparation and, in 2018, legal advice and teams spent around 40% of their GDPR budget, or $2.4 million, on UK FTSE 350 companies. (Forbes)
2. It has also been found that about 88% of companies spent more than $1 million on the preparation of their GDPR. (IT governance)
3. In the first year of GDPR, 1, 44,000 complaints were filed with various GDPR enforcement agencies, in addition to 89,000 data breaches. (EDPB)
4. Nearly 1,000 news sources blocked EU readers to avoid and hide GDPR compliance rules. (Nieman Lab)
5. You might not know that GDPR imposed a total of $63 million in fines in its first year. (GDPR.EU)
6. Google too could not escape the GDPR violations. A French data protection agency named CNIL fined Google $57 billion for GDPR violations. (TechCrunch)
7. A lot of companies have seen improvement after the implementation of GDPR Around 31% of consumers feel that their overall experience with companies has improved. (Marketing week)
8. As of 2019, only 59% of companies have claimed that they are GDPR compliant. (ZDNet)
9. Almost 70% of the companies absolutely agree that the systems put in place by them will not be big when the new GDPR rules come in. (Datagrell)
Historical Data Breaches Statistics (Cybersecurity Infographic)
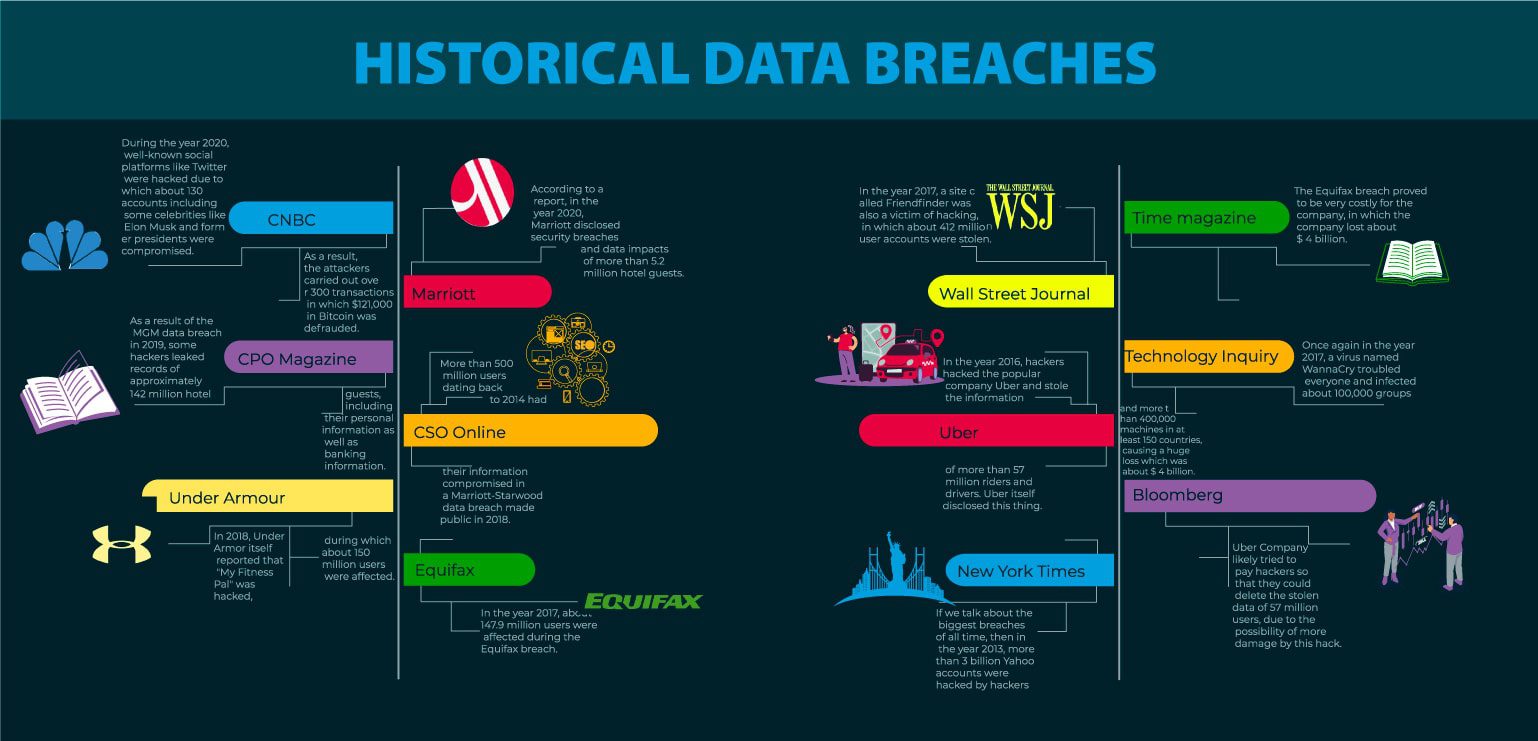
- During the year 2020, well-known social platforms like Twitter were hacked due to which about 130 accounts including some celebrities like Elon Musk and former presidents were compromised. As a result, the attackers carried out over 300 transactions in which $121,000 in Bitcoin was defrauded. (CNBC)
- According to a report, in the year 2020, Marriott disclosed security breaches and data impacts on more than 5.2 million hotel guests. (Marriott)
- As a result of the MGM data breach in 2019, some hackers leaked records of approximately 142 million hotel guests, including their personal information as well as banking information. (CPO Magazine)
- More than 500 million users dating back to 2014 had their information compromised in a Marriott-Starwood data breach made public in 2018. (CSO Online)
- In 2018, Under Armor, itself reported that “My Fitness Pal” was hacked, during which about 150 million users were affected. (Under Armour)
- In the year 2017, about 147.9 million users were affected by the Equifax breach. (Equifax)
- The Equifax breach proved to be very costly for the company, and it lost about $4 billion. (Time magazine)
- In the year 2017, a site called Friendfinder was also a victim of hacking, in which about 412 million user accounts were stolen. (Wall Street Journal)
- Once again in the year 2017, a virus named WannaCry troubled everyone and infected about 100,000 groups and more than 400,000 machines in at least 150 countries, causing a huge loss which was about $ 4 billion. (Technology Inquiry)
- In the year 2016, hackers hacked the popular company Uber and stole the information of more than 57 million riders and drivers. Uber itself disclosed this thing. (Uber)
- Uber Company likely tried to pay hackers so that they could delete the stolen data of 57 million users, due to the possibility of more damage by this hack. (Bloomberg)
- If we talk about the biggest breaches of all time, then in the year 2013, more than 3 billion Yahoo accounts were hacked by hackers (New York Times)
Statistics of Phishing Attacks (Infographic)
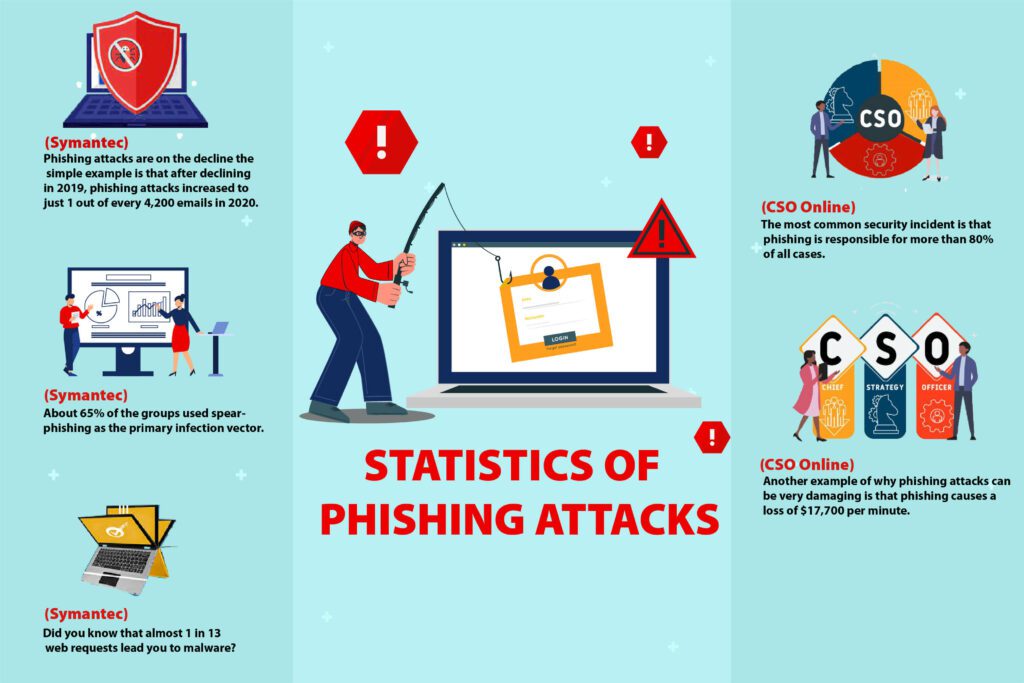
1. Phishing attacks are on the decline the simple example is that after declining in 2019, phishing attacks increased to just 1 out of every 4,200 emails in 2020. (Symantec)
2. About 65% of the groups used spear-phishing as the primary infection vector. (Symantec)
3. Did you know that almost 1 in 13 web requests leads you to malware? (Symantec)
4. the most common security incident is that phishing is responsible for more than 80% of all cases. (CSO Online)
5. Another example of why phishing attacks can be very damaging is that phishing causes a loss of $17,700 per minute. (CSO Online)
Statistics of Ransomware and Malware Attacks (Infographic)
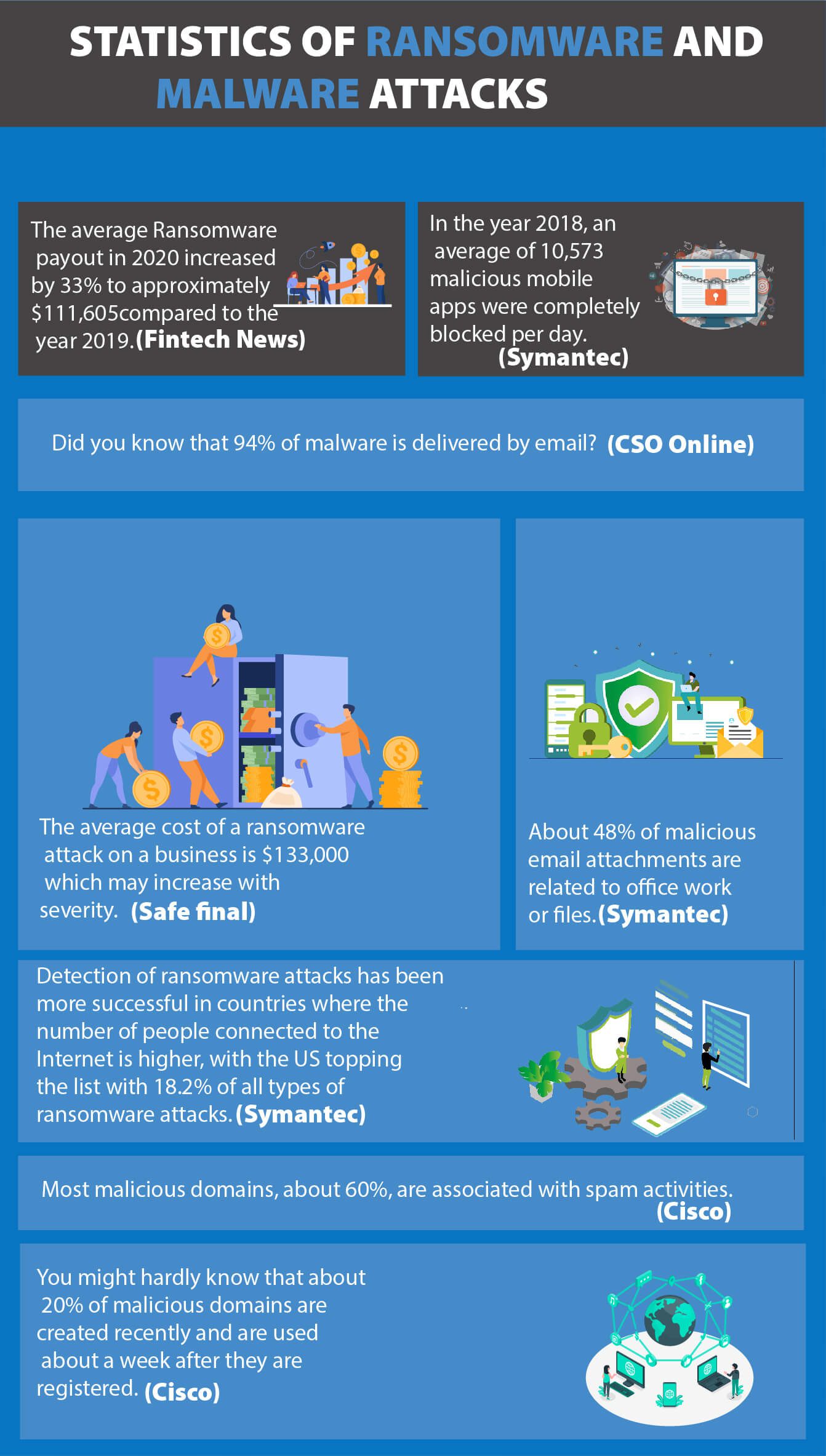
1. The average Ransomware payout in 2020 increased by 33% to approximately $111,605 compared to the year 2019. (Fintech News)
2. In the year 2018, an average of 10,573 malicious mobile apps were completely blocked per day. (Symantec)
3. Did you know that 94% of malware is delivered by email? (CSO Online)
4. The average cost of a ransomware attack on a business is $133,000 which may increase with severity. (Safe final)
5. About 48% of malicious email attachments are related to office work or files. (Symantec)
6. Detection of ransomware attacks has been more successful in countries where the number of people connected to the Internet is higher, with the US topping the list with 18.2% of all types of ransomware attacks. (Symantec)
7. Most malicious domains, about 60%, are associated with spam activities. (Cisco)
8. You might hardly know that about 20% of malicious domains are created recently and are used about a week after they are registered. (Cisco)
Statistics of IoT, DDOS, and Other Attacks (Infographic)
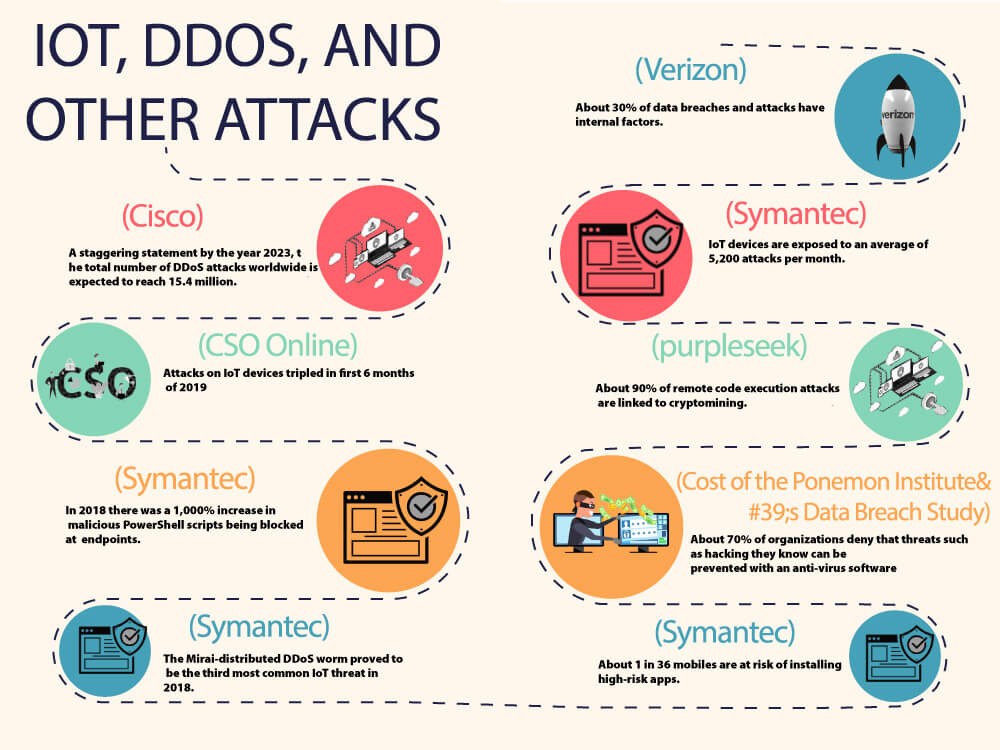
- A staggering statement by the year 2023, the total number of DDoS attacks worldwide is expected to reach 15.4 million. (Cisco)
- Attacks on IoT devices tripled in the first 6 months of 2019 (CSO Online)
- In 2018 there was a 1,000% increase in malicious PowerShell scripts being blocked at endpoints. (Symantec)
- The Mirai-distributed DDoS worm proved to be the third most common IoT threat in 2018. (Symantec)
- About 30% of data breaches and attacks have internal factors. (Verizon)
- IoT devices are exposed to an average of 5,200 attacks per month. (Symantec)
- About 90% of remote code execution attacks are linked to crypto mining. (Purpleseek)
- About 70% of organizations deny that threats such as hacking they know can be prevented with anti-virus software (Cost of the Ponemon Institute’s Data Breach Study)
- About 1 in 36 mobiles are at risk of installing high-risk apps. (Symantec)
Statistics of Cybersecurity Compliance and Governance (Infographic)
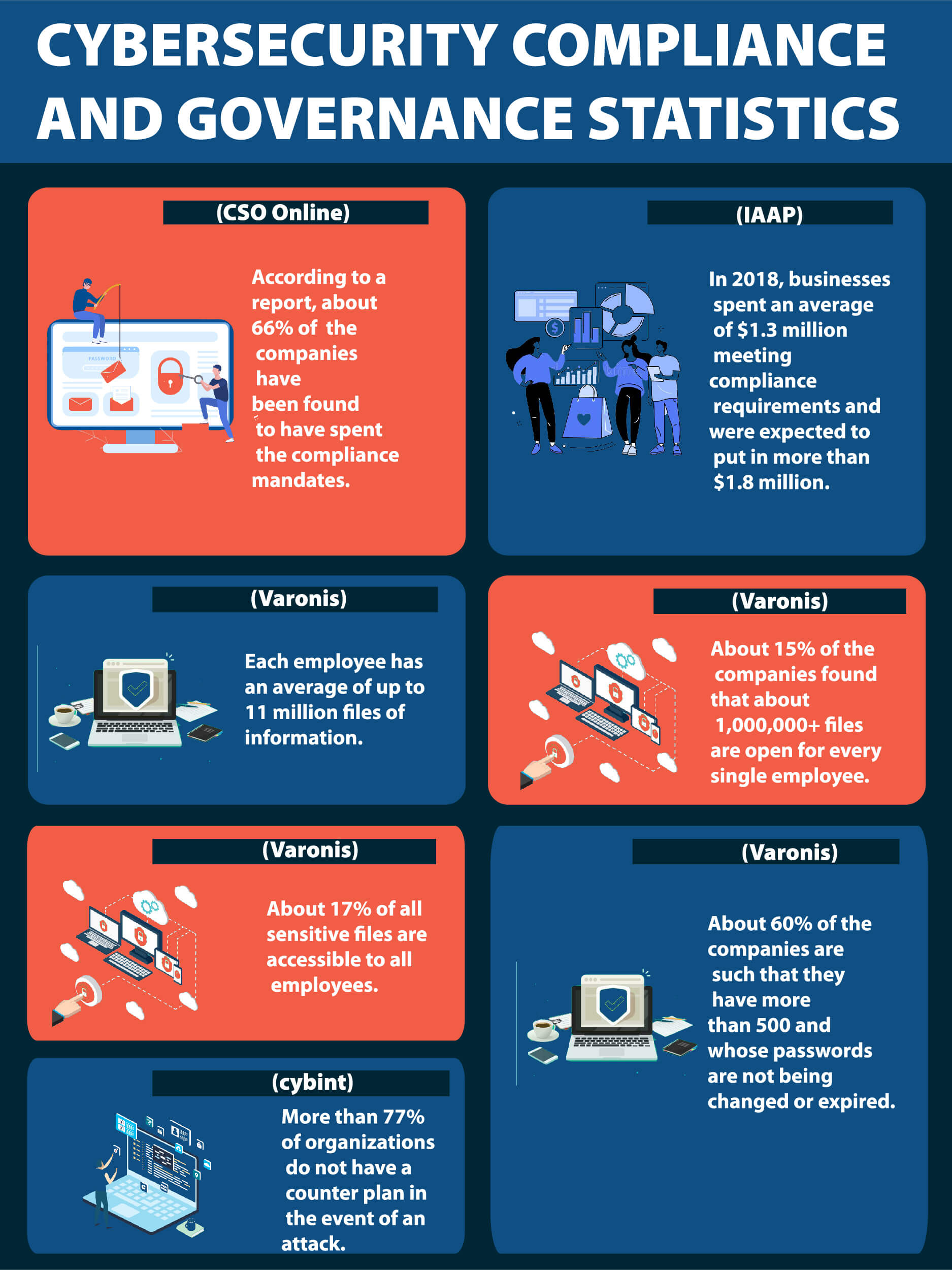
1. According to a report, about 66% of the companies have been found to have spent the compliance mandates. (CSO Online)
2. In 2018, businesses spent an average of $1.3 million meeting compliance requirements and were expected to put in more than $1.8 million. (IAAP)
3. Each employee has an average of up to 11 million files of information. (Varonis)
4. About 15% of the companies found that about 1,000,000+ files are open for every single employee. (Varonis)
5. About 17% of all sensitive files are accessible to all employees. (Varonis)
6. About 60% of the companies are such that they have more than 500 and whose passwords are not being changed or expired. (Varonis)
7. More than 77% of organizations do not have a counter plan in the event of an attack. (cybint)
6 Common Crimes And Risks Online According To the FBI (Infographic)
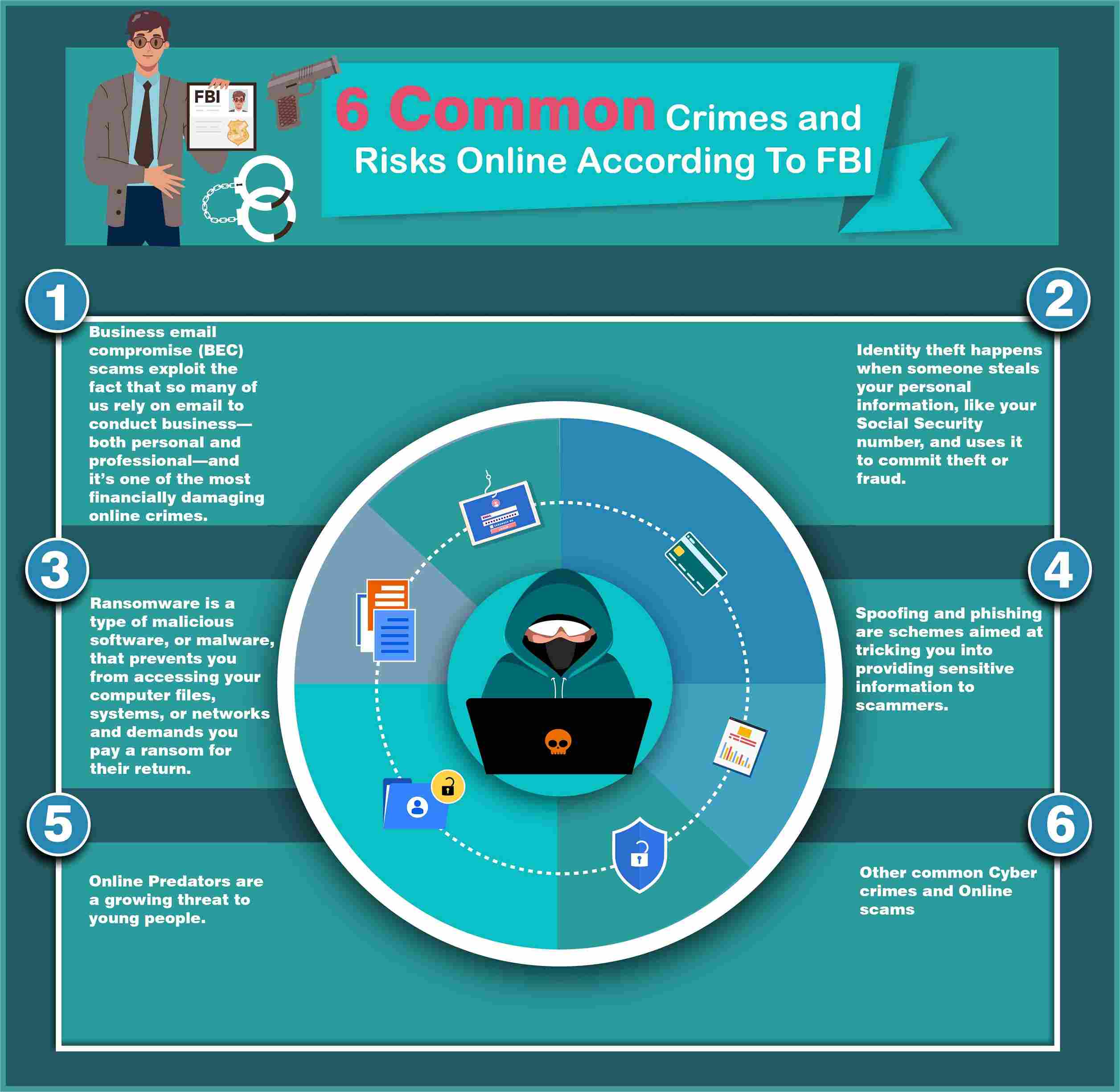
- Business email compromise (BEC) scams exploit the fact that so many of us rely on email to conduct business—both personal and professional—and it’s one of the most financially damaging online crimes.
- Identity theft happens when someone steals your personal information, like your Social Security number, and uses it to commit theft or fraud.
- Ransomware is a type of malicious software, or malware, that prevents you from accessing your computer files, systems, or networks and demands you pay a ransom for their return.
- Spoofing and phishing are schemes aimed at tricking you into providing the sensitive information to scammers.
- Online Predators are a growing threat to young people.
- Other common Cyber crimes and Online scams
Global Cyber Strategies Index (Infographic)

National Strategy: Overarching doctrine guiding national, coordinated deterrents and
responses to cyber threats.
Military: Strategies detailing offensive or defensive military capabilities in cyberspace.
Content: Laws regulating or restricting certain digital content.
Privacy: Strategies regulating the collection and handling of personal data.
Critical Infrastructure: Strategies for mitigating cybersecurity threats to critical infrastructure
networks and increasing resilience.
Commerce: Laws governing digital trade and the provision of Internet services.
Crime: Strategies or legislation for countering cybercrime
Cyber Attack Lifecycle Stages Involved in a Breach (Infographic)
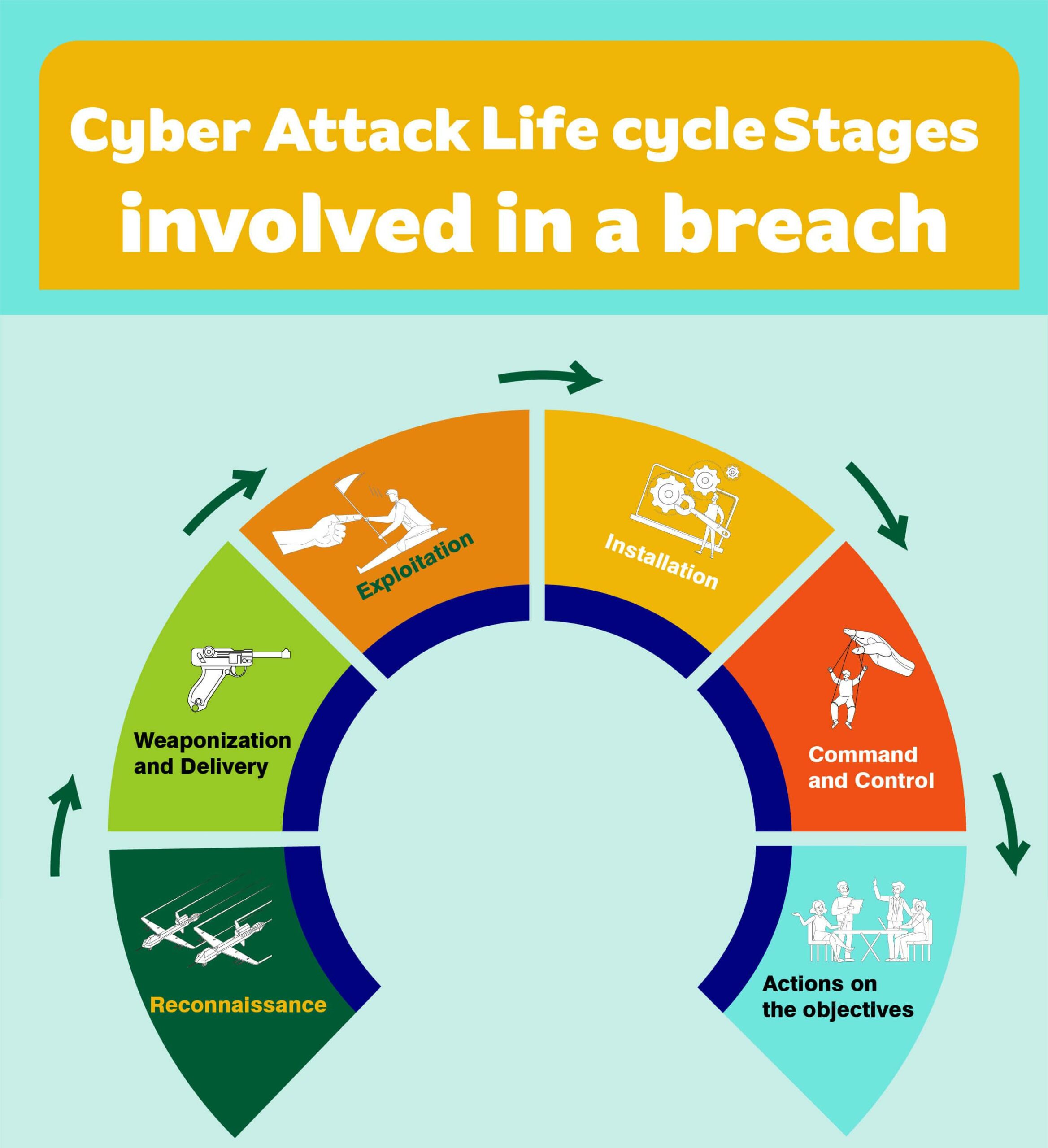
- Reconnaissance
- Weaponization and Delivery
- Exploitation
- Installation
- Command and Control
- Actions on the objectives
The Threat Intelligence Lifecycle (Infographic)
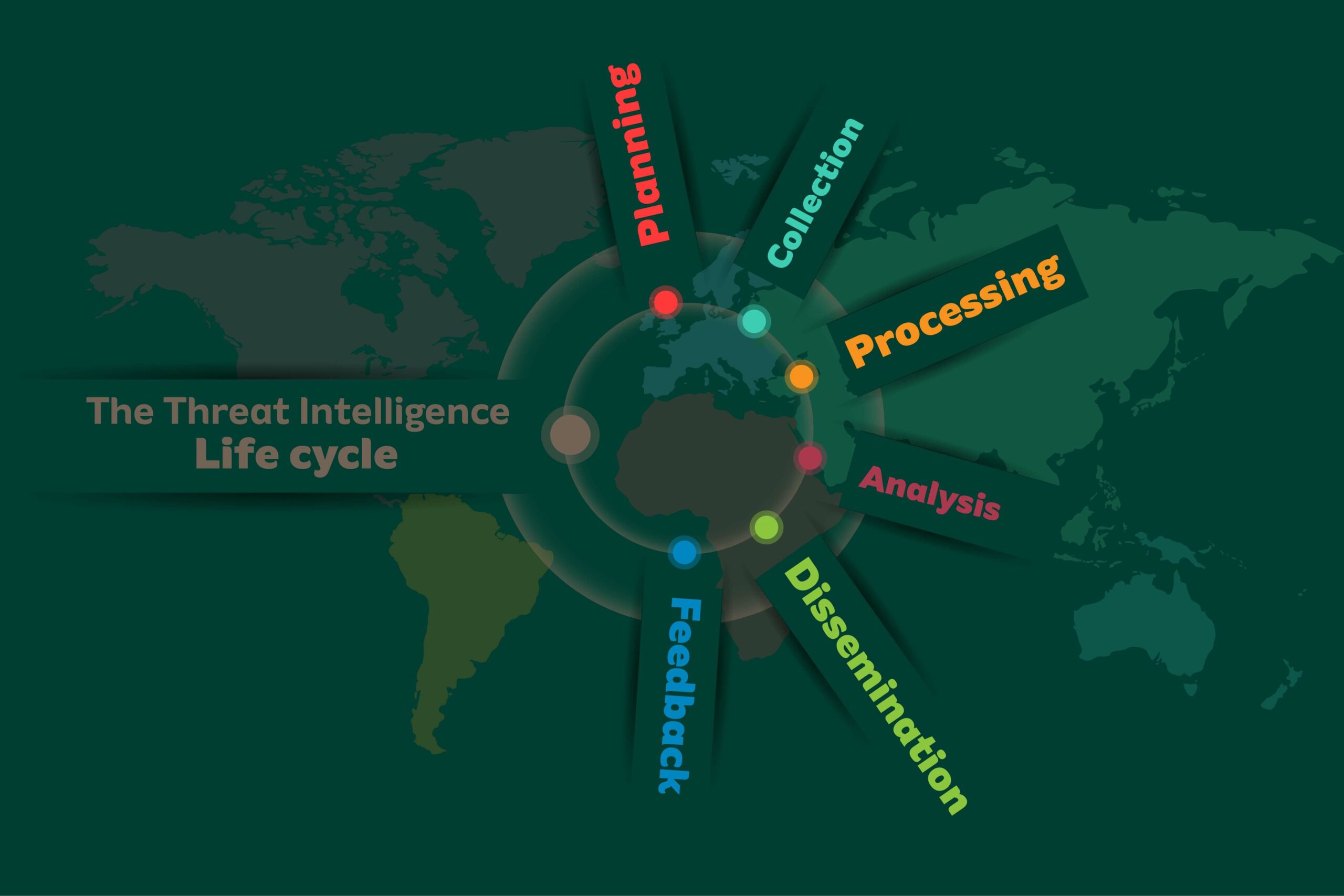
- Collection
- Planning
- Processing
- Analysis
- Dissemination
- Feedback
Types of Data Breaches (Infographic)
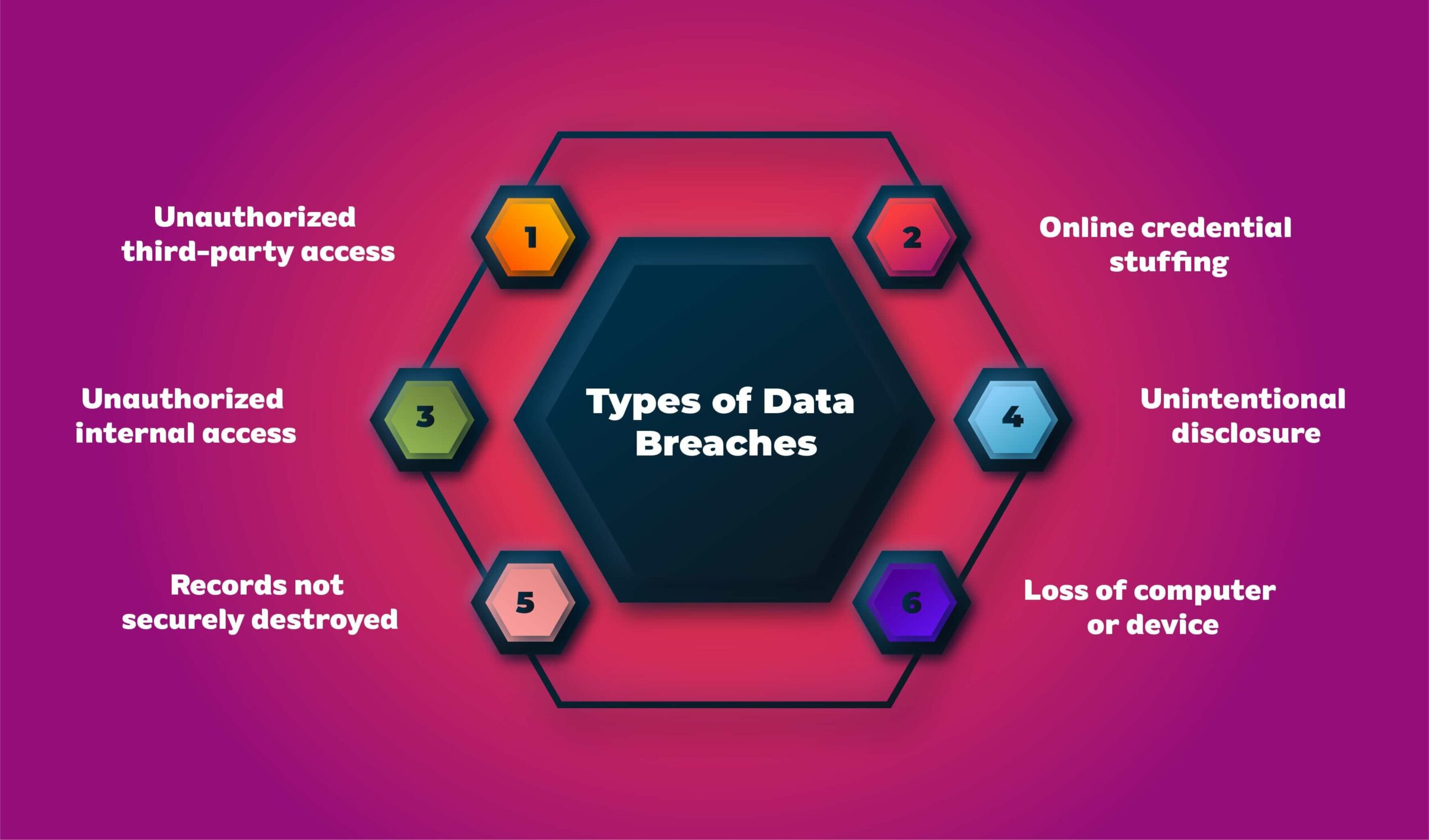
- Unauthorized third-party access
- Online credential stuffing
- Unauthorized internal access
- Unintentional disclosure
- Records not securely destroyed
- Loss of computer or device
Cybersecurity Essentials According To CISA (Infographic)
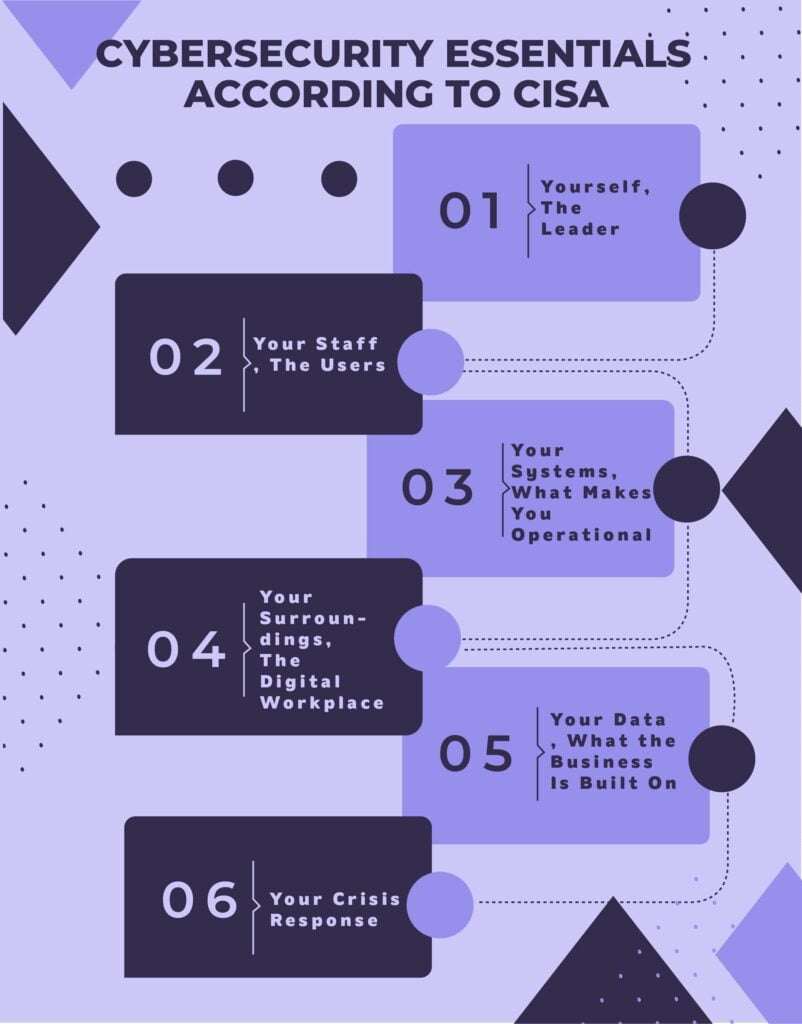
- Yourself, The Leader
- Your Staff, The Users
- Your Systems, What Makes You Operational
- Your Surroundings, The Digital Workplace
- Your Data, What the Business Is Built On
- Your Crisis Response

