In this article, we have made a comprehensive cybersecurity plan for small businesses.
In a world where data is shared across different mediums, the concept of privacy is significant for your business and your clients.
Continued trust in your business practices, products, and secure handling of your client’s confidential data can impact your profitability in the long run.
Each company is legally bound by a set of rules and policies that they need to adhere to. This is done to protect the confidential and sensitive data provided by customers.
A privacy policy is a pledge to your clients that you will use and protect their information in ways they authorize and adhere to your legal obligations.
Your policy should always clearly entail a clear statement clarifying the information you collect about your customers like physical addresses, email addresses, mobile numbers, etc., and how you use them.
Cybercriminals very efficiently target businesses irrespective of their business operations and sizes.
Nearly all cyber-attacks are intended to obtain personal data to identify theft. It is pretty apparent that extensive organizations have enough financial credibility to store and accumulate much more valuable data to steal.
Still, small businesses have less funding, are less secure, and have poor networks, making it easier to breach them.
Cybercriminals all over the world target corporations of various industries in the economy. Small firms’ networks are less secure, making it easier to infiltrate and steal personal information.
Almost all cyber-attacks are designed to gather personal information for use in cybercrime.
Implementing cybersecurity fundamentals and practicing them can help you defend your organization.
It can lower the danger of a cyber attack. It is critical to safeguard your business from cyberattacks, but many individuals are unaware of how to do it. So, we prepared this blog to help you know about the cybersecurity plan for small businesses.
Table of Contents
What is a Cybersecurity Plan?
A cybersecurity plan sets out certain policies, procedures, and strategies required to protect a business organization against its threats and risks.
A cybersecurity plan has to outline the specific actions needed to respond to a security breach.
Cybersecurity is the application of technologies, processes, and controls to safeguard systems, devices networks, programs, and sensitive client data from cyber-attacks.
A strong cybersecurity plan aims to lessen the risk of cyber-attacks and protect the organization against unauthorized network breaches from hackers.
The cybersecurity plan/strategy also establishes a concrete foundation for a company’s security program, continuously adapting to emerging threats and risks.
As a business owner, it’s exclusively your responsibility to clarify and disclose all policies of your company, and only you will be held accountable.
That’s why it’s important to create your privacy policy with consideration and post it clearly on your business site.
It’s a necessity to protect your business from such breaches and increasing cyberattacks, but some business owners aren’t sure how to do that.
Implementing a cybersecurity plan and putting them into practice will help you protect your business and lessen the risk of a cyber attack.
Customers, employees, and business owners constantly expect you to prioritize their privacy.
There are also a growing number of rules and regulations safeguarding consumer and employee privacy and often result in costly penalties for privacy breaches.
A well-orchestrated cybersecurity plan can give a good security posture for businesses. It helps against malicious assaults designed to access, modify, delete or steal computers and sensitive data.
How to Develop a Cybersecurity Plan for Small Business?
Before you get into the depth of developing a cybersecurity plan, it’s crucial to understand why a strategy is needed and why are cybersecurity plans so significant.
Creating and implementing a cybersecurity plan in the organization is crucial because Cyberattacks have exponentially increased over the pandemic period.
There have been no evident signs showing that the attacks have ceased, and evidence supports that these cyber attackers will only continue to attack vulnerable systems unless there are robust policies and regulations established to curb them.
An important element of an effective security strategy is the knowledge of how a security policy works.
Security policies are a set of written conventions and procedures that all employees must follow to ensure the confidentiality, integrity, and availability of confidential data and resources.
What Should Be Included in a Cybersecurity Plan?
In simple terms, the cybersecurity plan or policy lays out the expectations for the industry and how they are to be achieved. It also describes the consequences of failure in intending to protect the organization.
The following elements should be in place to prevent breaches from continuing, react quickly to unforeseen incidents, and mitigate their impacts.
A cybersecurity plan should include all the below-mentioned points so your organization can respond effectively to a security breach.
Develop a Security Policy for Small Business
Prevention is always better than cure. The best incidents are those that have never really happened. If a company has its security policies laid out, that can effectively prevent a breach from taking place.
To never attain a catastrophic breach, make sure your essential security systems are running in the best form.
One needs to keep in mind that these policies need to be formed beforehand to minimize the risk and losses resulting from cybersecurity breaches. These include:
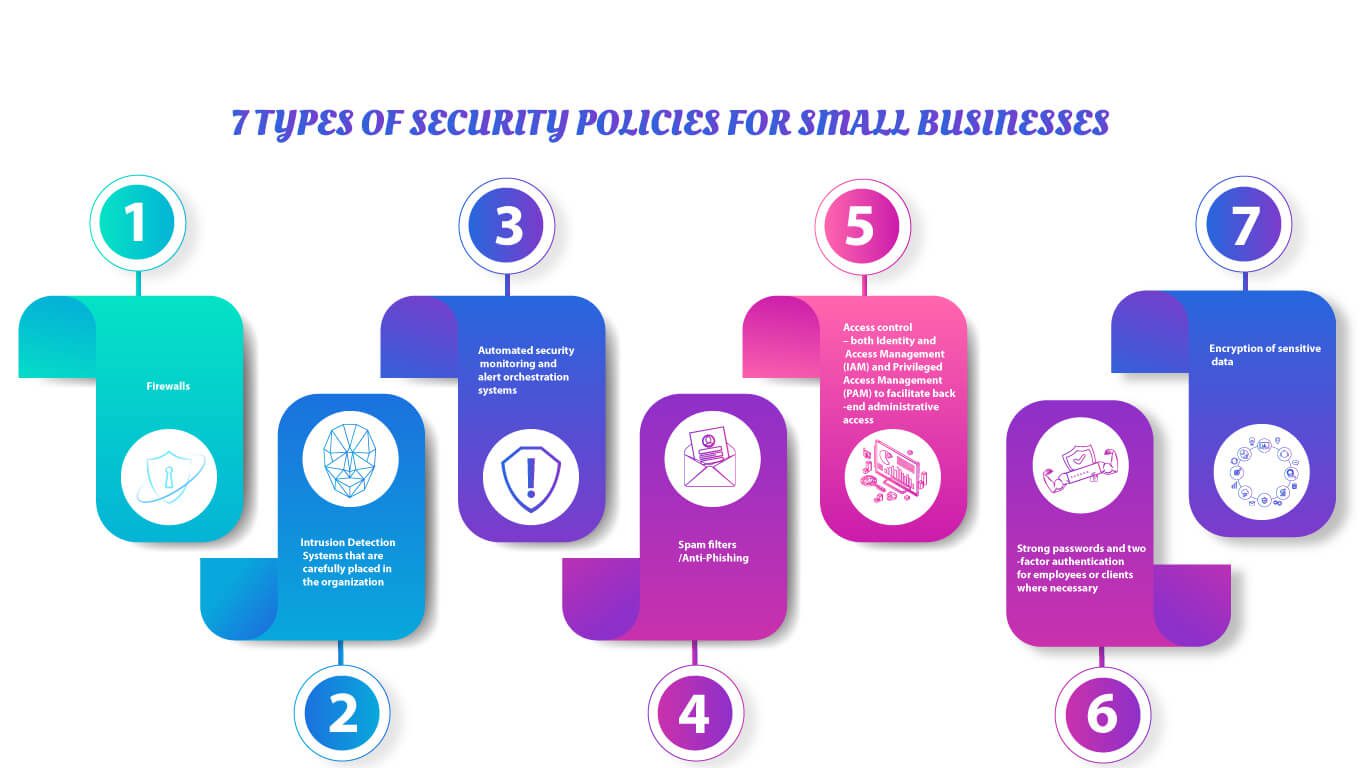
7 Types of Security Policies
- Firewalls
- Intrusion Detection Systems that are carefully placed in the organization
- Automated security monitoring and alert orchestration systems
- Spam filters/Anti-Phishing
- Access control – both Identity and Access Management (IAM) and Privileged Access Management (PAM) to facilitate back-end administrative access.
- Strong passwords and two-factor authentication for employees or clients where necessary
- Encryption of sensitive data
Unite with Internal Stakeholders
In the event of an unforeseen cybersecurity breach, personnel and employees in the company’s IT, finance, legal, and other departments should be ready at a moment’s notice.
Each individual should have a pre-assigned role related to incident response. Eliminating guesswork will assess the situation without wasting any valuable time.
All employees should be trained to recognize the signs of a possible breach.
If required, they will be able to recognize tactics such as hacking methods used to mislead people into providing personal details, installing malicious software on the network, or allowing the hacker to steal information.
Operate within a framework
The cybersecurity team must adapt to the sorts of data protected and the circumstances at hand that are involved. A solid framework is an important component of cybersecurity risk management.
This framework should equip you with the plan needed to negotiate a cybersecurity incident without any assumptions or delay.
The framework should span all work processes, employees inside and outside the company, including third-party vendors as well as systems that are connected to your corporate network.
Be Aware of Threat Intelligence
It is extremely useful to analyze and make informed decisions during a breach. One needs to recognize the signs of an attack and the tactics, procedures, and techniques, using predetermined indicators as a reference.
Threat intelligence comprises these indicators, context, and actionable insights into existing and emerging threats to the assets of these companies.
The knowledge included here is based on evidence, providing the basics to making informed decisions when a cyber incident starts.
Vulnerabilities such as shared administrative passwords, open and unprotected software and operating systems, device configurations, or business operations and processes provide a context to the threat.
Identifying the accidental or intentional acts of an individual staff member will also provide the threat intelligence needed to respond to a cybersecurity incident appropriately.
Understand Regulatory Factors and General Liability
A response to a breach should consider regulations about your industry niche. For instance, if your organization is determined to have been negligent in its handling of security, there could be legal and regulatory ramifications.
Having an explicit audit log of what happened before, during, and after the breach may prove quite helpful to clear your organization of the charge of negligence in its security duties.
Conducting a Risk Assessment
The actions taken should also include the appropriate guidelines that are outlined in the model.
Once cybersecurity threats are prioritized, the steps to tackle each one as it occurs are more transparent to all shareholders involved. Risk assessment doesn’t only fine-tune your cybersecurity comeback but also helps prevent attacks in the first place.
It involves positioning oneself in the mind of an attacker and trying to think what is the next possible step they might take.
If you can determine what may be most practical to them, it’s more evident where to focus your resources to protect the most vulnerable and confidential data.
Each cybersecurity plan should be tested and kept up-to-date. Outdated cybersecurity breach response plans are likely to be ineffective.
If all the elements of your cybersecurity plan are in place, you can alert all the employees and risk management programs related to cybersecurity at a moment’s notice.
Visibility is another key factor when a breach can occur. It’s best if you can see who has accessed the network, what systems, and at what time did something go wrong to gather as much intel as possible.
In addition to a single Information Security Policy, many organizations choose to have specific policies instead of one extensive policy.
Below are sample policies that can be written and the main security policy.
Workstation Policy
Antivirus for systems and devices, General security, unattended access and device lock, confidential password, software patching, biometrics, etc.
Acceptable Use Policy
- Internet browsing and usage
- E-mail usage within the organization
- Usage of social networking sites
- Electronic file transfer of confidential information and customer data
Remote Access Policy
- Definition of remote access to each employee
- Who is permitted to access the data and sites within a network, including vendors and clients
- Types of permitted devices and operating systems within the network.
- Methods permitted (SLVPN, site-to-site VPN)
A Comprehensive Cybersecurity Plan For Small Businesses
Here are some of the points to consider while establishing a cybersecurity plan for your small business.
Set up a security policy
Create IT cybersecurity rules and practices for your company. It includes enforcing secure passwords and adopting proper internet usage guidelines. These help to cover your company’s cybersecurity policy in detail.
Security measures ensure that employees in your organization are on the same level. It can be helpful in handling, consumption, and storage of company data.
They also make certain that your IT professionals adhere to suitable and agreed measures to protect data and prevent infrastructure.
Your security policy should come from the highest level of your IT organization. They should properly communicate it to all of your employees and contractors.
Security policies should be effectively incorporated throughout your organization’s procedures. They have to be communicated and successfully implemented by all its employees.
Investing in Training Employees
Employee education is the first key to protecting your client’s data. For instance, even if your company has an official password policy, it won’t help safeguard your information if your employees and stakeholders are not completely compliant.
Make this education mandatory for your employees and shareholders, and be sure to review and update your training material annually to stay up-to-date on the latest risks and potential threats.
Closely Monitor Activities in Your Business Environment
To enforce high-quality security best practices across your enterprise, it’s also important that you actively monitor all that your employees do. This can include measures such as:
Regardless of your business size, you will want to execute these essential technical controls.
Monitoring staff actions is also important for assessing and enforcing best security practices across your company.
Tracking events such as account creation and logins helps you spot unusual activity and participate in active malware detection.
Extending your audit procedures to include all sensitive data repositories in your private network, such as file servers, SQL database servers, and so on.
Maintain a lookout on both attempted access and actions involving sensitive data. Always monitor log files to cloud services, and user activity on them.
Passwords and Authentication
Weak passwords can allow hackers to access and control multiple accounts through a single-password domino effect. However, as debated earlier, a potent password policy eliminates this key vulnerability.
Depending on the security of your office and internet network security requirements, you might want to tweak your password policy with cybersecurity rules like multifactor authentication, which strengthens passwords by requiring one or more extra forms of authentication.
Remember that a password policy is only as strong in how you enforce it. Here are some best practices to ensure that your clients and employees stay in compliance with demanded standards, such as locking user accounts automatically after various unsuccessful password attempts.
You can also Identify accounts with no password requirements (or passwords that never expire) and constrict these authentication requirements according to your business policy.
Strong passwords are simply a complicated collection of special characters, numbers, and letters. These increase the security of all your online accounts.
Make it a requirement for all workers to utilize two-factor authentication whenever they access critical corporate data. It’s also a good idea to encourage them not to reveal their usernames to unauthorized people.
Weak passwords can allow malicious attackers to access and control many accounts via a single-password effect.
Depending on your office’s multi-factor internet security needs, you can choose to supplement your password policy with cybersecurity rules such as multi-factor authentication, which strengthens passwords by requiring one or more forms of verification.
Adding multi-factor authentication to your company’s accounts can protect you from many serious attacks on your data. Many users use the same password for many accounts despite warnings to the effect.
In the absence of Multi-Factor Authentication, a single hacked password can grant an attacker access to several corporate accounts.
Email Security
Email communication can easily become a vulnerable attack surface for cybercriminals and malware, as negligent or oblivious users are frequently tricked into opening dangerous links embedded within messages.
Employee education that covers topics like phishing and malware can help boost the security of your small business’s email channels.
Additional protective measures include message encryption, along with spam filters and suspicious antivirus software that can filter out potential threats before they can reach unsuspecting users.
System and Network Security
Be sure to equip your IT systems with the most up-to-date security features by regularly installing patches and updates for your organization’s software and hardware.
Always keep a close eye on changes and events on your systems, including file-sharing systems and database servers.
You will also need to build your company’s network perimeter with appropriate antivirus software and firewalls and configure your internal Wi-Fi connection to maximize mobile security and protection.
Set up secure and private VPN tunnels to enable remote access to those employees who work primarily with IT.
Check that your Wi-Fi network is safe, encrypted, and hidden. To hide your wireless network, configure your router not to broadcast the network name and secure its access with a strong password.
Unsecured Wi-Fi exposes your network to hackers, so change Wi-Fi passwords regularly. To ensure network security, separate guest and corporate wireless networks and consider restricting the length of visitor network sessions.
Ensure your IT systems have the most up-to-date security features by regularly applying bug fixes for your organization’s software and hardware.
Always stay updated on changes and access events on your essential systems, such as file-sharing systems and database servers.
Harden your network’s perimeter with proper firewalls, and design your internal Wi-Fi connection to enhance mobile security and antivirus software. Establish secure VPN tunnels for remote access to IT sources.
Secure Your Infrastructure
Small businesses should include a range of effective technologies and techniques for protecting their IT infrastructure from cyber attackers. Designing and managing complex security technologies can be a time-consuming and expensive task.
Firewalls should be your next protection and can be independent systems or integrated into other devices such as routers or servers. They are also accessible as both hardware and software solutions.
Choose an anti-malware software that has both enterprise security and anti-spyware capabilities. This software scan detects and removes malware from your systems and devices. You can install it on PCs, gateway servers, or dedicated network appliances.
Users can encrypt gadgets, emails, and data with encryption solutions. Encrypting devices protects the data stored on them if stolen, lost, or misused.
Encrypting emails ensures that your data is secure even if your email account or authentication credentials are compromised. It is also valid for data; encrypting data ensures that it stays secure from unauthorized individuals.
Backup software that creates an off-site backup can help you assure company continuity and never have to pay excessive fees to attackers.
Tracking changes and accessing events directly or utilizing your system’s inherent capabilities is inconvenient and time-consuming.
Time is a valuable resource that small businesses lack. It helps to access events and keeps you warned about danger patterns. Also, helping you understand the present health of your infrastructure is critical for your security.
10 Key Cybersecurity Tips To Protect Your Small Business
- Train employees in security principles
- Protect information, computers, and networks from cyber attacks
- Provide firewall security for your Internet connection
- Create a mobile device action plan
- Make backup copies of important business data and information
- Control physical access to your computers and create user accounts for each employee.
- Secure your Wi-Fi networks
- Employ best practices on payment cards
- Limit employee access to data and information, and limit authority to install software
- Passwords and authentication.
The Business Case of Cybersecurity For Your Organization
- Understand the business’ security posture
- Identify business assets that need to be protected
- Align security investments to business objectives
- Determine the right areas for investment
- Implement a security plan and schedule
- Preparation
In a Nutshell
To sum up all of the information discussed, we know that cyber-criminals work extensively across different organizations and attempt to steal data.
They very efficiently target firms irrespective of their business operations and sizes. And therefore, a robust cybersecurity plan goes a long way to strengthen the company’s credibility and safeguard your client’s data.



