In this age of cyber-terrorism, online security is more important than ever. One of the most important tools for protecting your computer and your data is a firewall. But what is a firewall, and how do you know if you need one?
In this blog post, we’ll answer those questions and more. We’ll also give you some tips on how to choose the right firewall for your needs. So read on to learn everything you need to know about firewalls!
Table of Contents
What is a Firewall?
A firewall is a security system that controls the flow of incoming and outgoing traffic on a network. Firewalls can be software-based or hardware-based and is a part of cybersecurity.
It is an important part of your organization’s defense against cyber attacks. Now, let’s discuss the basics of firewalls and how they can help protect your organization’s computer networks- shall we?
How does it work?
A firewall is a device or software application that helps protect your computer network from unwanted access and intrusion. It works by blocking incoming and outgoing traffic based on predefined rules.
They can be used to protect a single computer, a whole network, or even the internet as a whole.
You have the leverage to implement firewalls on both hardware or software realms, or a combination of the former two at once. They will function in accordance with the type and level of protection one requires.
Types of Firewalls
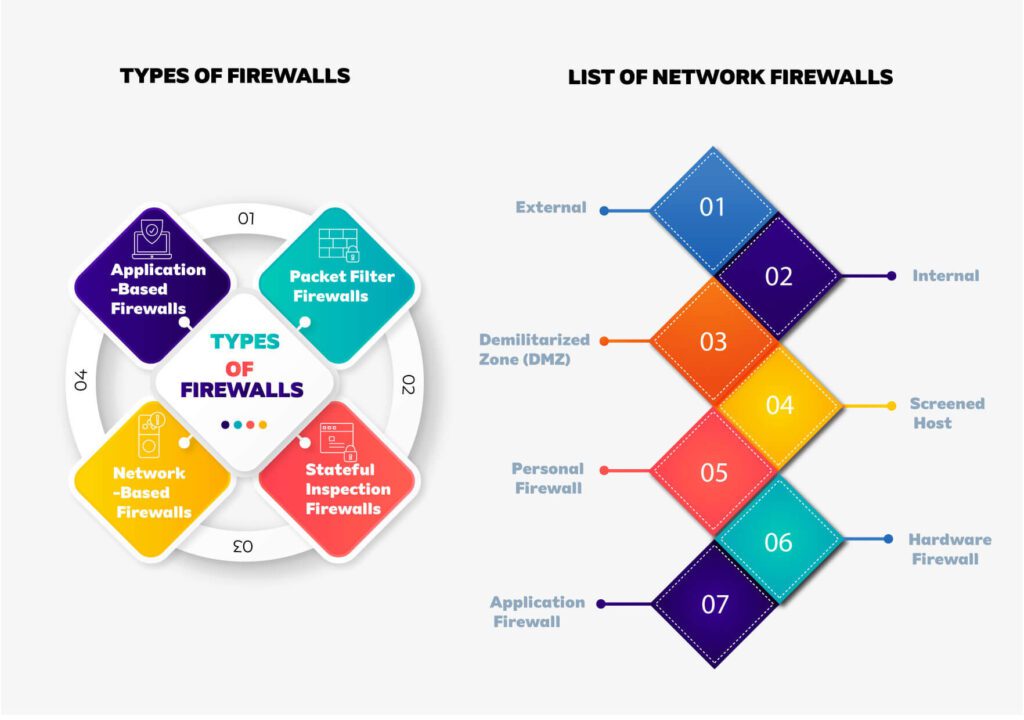
Packet Filter
This is the most basic level firewall that examines each packet (a piece of data) that goes in and out from your computer to determine if it’s allowed through.
If the packet doesn’t meet the specific criteria of the firewall rules, it’s blocked and discarded. This type of firewall is easy to set up but offers limited protection.
Stateful Inspection
This type of firewall is more sophisticated than a packet filter firewall and can track the state of packets (such as which ones are part of an ongoing conversation).
This helps to ensure that all packets passing through the firewall are legitimate and authorized. Stateful inspection firewalls offer better protection than packet filter firewalls but can be more complex to set up.
Application-Based
Application-based firewalls work by controlling specific applications (such as your web browser) rather than all network traffic.
This is useful if you want to allow certain types of traffic but block others, such as giving your employees access to the internet for research purposes but preventing them from wasting time on social media websites.
Network-Based
Network-based firewalls work by monitoring network packets that go in and out of your computer. They are commonly used in businesses and other organizations to protect their networks from unauthorized access.
What is the Importance of a Firewall?
A firewall is an important security tool that helps protect your computer or network from unauthorized access and attacks. It does this by blocking incoming and outgoing traffic based on a set of rules that you specify.
As we know from previous discussions, a firewall can be hardware-based in nature, sometimes software-based too, or a combination of both as per the level and type of security demands.
Hardware-based firewalls are typically devices that are installed in between your computer or network and the Internet.
They work by inspecting all traffic that passes through them and allowing or denying it based on the rules you’ve set up. Software-based firewalls are applications that run on your computer and act as a shield against unauthorized access and attacks.
They work by inspecting traffic as it comes in and out of your computer and allowing or denying it based on the rules you’ve set up.
Advantages and Disadvantages
The main advantage of using a firewall is that it provides a layer of security between your computer or network and the outside world. This helps to protect you from malicious attacks, such as viruses, worms, and hackers.
It can also be used to block certain types of traffic, such as p2p file-sharing or streaming media, from crossing over into your network. This can help to improve performance and reduce the amount of bandwidth that is used.
However, there are also some disadvantages to using a firewall. One is that it can sometimes interfere with legitimate traffic, such as when you are trying to access a website that is blocked by the firewall.
Another disadvantage is that it can be difficult to configure a firewall correctly so that it provides the desired level of security without interfering with regular traffic. Additionally, it can be resource-intensive, which can slow down your computer or network.
Ultimately, the decision of whether or not to use a firewall is up to you. But, if you are not already using one, it is a good idea to at least consider installing a firewall on your computer or network. So, those are some of the pros and cons of using a firewall.
What is a Managed Firewall?
A managed firewall is a stateful, application-layer firewall that allows or denies connections based on the configurable policy.
It can enforce which applications are able to communicate over the network through direct access to RFC 1918 addresses (private Internet addressing).
The most common use of a managed firewall is for Internet-facing interfaces protecting DMZ subnets. Please note that it cannot be used as an edge-based security device.
The following example illustrates how traffic flows through a managed firewall configured with two ISP links and one corporate LAN:
It allows only HTTP and HTTPS traffic between the corporate LAN and the rest of the world so machines on either side can’t ping each other by default unless their traffic matches some rule(s) in your configuration.
What are the benefits of using a Managed Firewall?
- Security – a firewall can help protect your network from unauthorized access;
- Compliance – firewalls can help you meet compliance requirements, such as PCI DSS or HIPAA;
- Performance – a managed firewall can make sure that network traffic for critical business applications receives priority over other types of traffic.
Managed vs Unmanaged Firewall- Explained
The managed type means that you can configure all of its settings yourself and change them to your will, but every time it gets compromised, you have to reinstall the firewall or update it with new patches.
The unmanaged type means that the firewall is set up by default and you can’t change any of its settings, but it’s also very stable and secure.
The main difference between these two types of firewalls is that a managed one can be customized to your needs, but at the same time it’s more vulnerable to attacks since you’re in charge of its security.
An unmanaged firewall is more secure, but you can’t change any of its settings. So, it all comes down to what you need and how much protection you want.
If you’re not confident in your ability to keep a managed firewall safe, then go for an unmanaged one. Otherwise, if you know what you’re doing and you want more control over your firewall, go for a managed one.
In conclusion, both types of firewalls have their own advantages and disadvantages, so it’s up to you to decide which one is best for you.
Just remember that no matter which type you choose, it’s always important to keep it updated with the latest patches and to have a reliable antivirus installed as well.
What is Network Firewall Security?
If a packet matches a rule, the firewall allows or blocks the packet based on the rule’s settings. So, a Network firewall security is a process of securing a computer network by protecting it from unauthorized access and attacks.
A network firewall is a type of security system that monitors and controls the incoming and outgoing network traffic based on predefined security rules
List of Network Firewalls
External
Checks all traffic as it passes through the router and allow or deny entry to the network as needed based on a set of configurable rules.
This type of system is typically installed at the edge, or boundary, of a network and can be likened to security personnel who stand between two friendly countries to prevent conflict.
Internal
Monitors all traffic as it passes through the router and allows or denies access to the network based on a set of configurable rules. It is more commonly referred to as a bastion host and is typically used in corporate networks.
DMZ
Stands for Demilitarized Zone and is an area of a network that is accessible to both authorized and unauthorized users. All traffic passing through a DMZ is typically inspected by a firewall, which allows or blocks the packets based on predefined security rules.
Screened Host
Similar to a DMZ, a screened host provides access to authorized and unauthorized users, but all traffic is inspected by a firewall before it is allowed to enter the network. It is often used in conjunction with a DMZ to provide an extra layer of security.
Personal
A personal firewall is a software application that resides on a single computer and protects that computer from unauthorized access and attacks. It is often used in conjunction with a software proxy to provide additional security.
Hardware
A network appliance that works at the intersection points of a private network and provides protection from unauthorized access and attack. A hardware firewall can be installed on a router, switch, or other devices.
Application
A firewall that is designed to protect specific applications from unauthorized access and attack. Application firewalls are commonly used to protect web applications and email servers from attacks.
The most important factor in choosing a firewall is the type of traffic it will be inspecting.
For example, if you are trying to secure a network that only consists of Linux machines, you would not need a firewall that can inspect Windows traffic, as the machines will not be able to generate that type of traffic.
Similarly, if you are trying to secure a network that contains both Windows and Linux machines, you would need a firewall that can inspect both types of traffic.
The next most important factor is the level of security that is required. For example, if you are only trying to secure a small network, a personal firewall may be all you need.
If you are trying to secure a large network, you will likely need a more robust firewall solution, such as an external firewall or a screened host firewall.
Finally, if you are trying to secure a network that consists of both external and internal machines, an internal firewall may be the best solution for your needs.
Security levels vary greatly between different types of firewalls. For example, personal firewalls are typically not as secure as screened host or DMZ firewalls.
When choosing a firewall, it is important to consider the security needs of your organization and select the best one that provides the appropriate level of security.
List of Managed Firewall Security Services
Almost all companies use managed firewall services to protect their networks and data from intrusion.
A managed firewall service provider helps the company to set up, configure and manage their network security devices like firewalls, routers or switches, which helps them in fighting against cyber-attacks.
There are two main types that can be managed, and the providers provide their services accordingly. As we already know, these are network-based firewalls and host-based firewalls.
Network-based firewalls are located on the border of the public and private networks, while host-based firewalls work by inspecting all packets entering or leaving a device (such as a desktop computer) to see if there is any suspicious activity or virus that needs to be blocked.
Network-based firewall service providers offer their service in different ways. They may offer to manage an entire company’s network by performing audits, installing security patches, reporting breaches, etc.
They may only provide firewall equipment (e.g., hardware appliances) for businesses to install themselves internally on their own networks. Host-based firewall services typically offer additional features
In today’s Internet-centric world, there are many security threats that you have to deal with. Many organizations prefer managed firewall services because they are more efficient than the traditional firewall solutions in use.
The list below includes some of the biggest names in the business of managing firewall services, including:
- CISCO
- Dell
- Fortinet
- Juniper
- MacAfee
Cisco Firewall Services Module (FWSM) Patching is one of the most important security measures for any organization. The only problem with patching is that it can be difficult and cumbersome, depending on the size of the organization.
Cisco has a solution for this. Cisco provides firewall services that are cloud-based, and the company claims that it is “the fastest, most reliable and easiest way to deploy and manage firewall services”.
Using this service is easy, and they can significantly reduce the time and cost of deploying regular patches.
Dell SonicWALL Global Management System (GMS) SonicWALL GMS combines powerful network security, management and threat protection with the flexibility of the modern cloud-based architecture. It is intuitive, easy to use and deploys in minutes.
Featuring powerful management capabilities and virtualization support, SonicWALL GMS delivers a truly integrated solution that provides secure remote access and dynamic network segmentation while simplifying the management of multi-vendor networks.
Fortinet’s FortiGate M Series Integrated Security Appliance combines the simplicity of a firewall with the flexibility of a multi-threat security platform, including a next-generation firewall, application control & Web filtering, IPS, anti-virus, anti-spam and URL filtering.
The FortiGate M Series ISA is a fully integrated security appliance that provides firewall, VPN, IPSec, SSL VPN gateway and UTM functionality. It’s designed to be deployed in small offices with up to 50 users.
The FortiGate M Series is available in four models: the M100D, M200D, M300D and the M400D. Each model has a different number of interface slots, ranging from one to four.
Regardless of the model you choose, all of them provide the same level of protection. The difference is how many interfaces each model can accommodate.
Juniper Networks Secure Access Service (JUNOSaaS), a provider of networking and security technologies, has its best service when it comes to firewalls, Juniper Networks Secure Access Service (JNSA).
It’s an innovative, cloud-native service that delivers secure access to the applications and data that users need to do their jobs. It also helps organizations meet compliance mandates such as GDPR and NIST FIPS 140-2.
McAfee Virtual Threat Protection Service is a well-known cybersecurity solution provider.
Their Virtual Threat Protection Service is a cloud-based service that protects computers and networks against cyber-attacks and malicious files.
It gives users a real-time view of the security threats present on their system and also provides an option to remove them.
Conclusion
It is important to have a firewall in place to protect the data of your organization. If you are not using it for protection, it’s high time you start thinking about it. As per our understanding, the easiest way to implement a firewall is with a virtual appliance.