Cloud security is a term that we hear more and more of as our world becomes increasingly digitized. But what is it, exactly? And how can you be sure your data is safe when it’s in the cloud?
In this post, we’ll demystify cloud security and explore how to best protect your information. Stay safe out there!
Table of Contents
How Does Cloud Security work?
Cloud security is a complex topic, and there is no one-size-fits-all answer to this question.
However, in general, the cloud provider takes on the responsibility of securing the infrastructure while the customer is responsible for securing their data.
The cloud provider will typically have a range of security measures in place, such as firewalls, intrusion detection systems, and malware protection, to protect the infrastructure.
The customer is responsible for ensuring that their data is encrypted and that they are using strong passwords and authentication measures.
The customer is also responsible for establishing policies and procedures through governance to ensure that the organization complies with regulations.
The security responsibilities are typically split 50/50 between the cloud provider and the customer, but it is important to remember that different cloud providers may have different levels of security responsibility assigned to each party.
For example, some cloud providers are completely responsible for securing the infrastructure while others are only responsible for securing the data.
It is also important to remember that the cloud is not a silver bullet and cannot solve all your security problems.
You still need to have strong security measures in place on your own network to protect your data from unauthorized access and theft.
What are The Types of Cloud Security?
Cloud security can be generally classified into three types: data security, platform security, and governance.
Data security is the practice of protecting your data from unauthorized access or theft.
This includes ensuring that your data is encrypted when it’s sent to and from the cloud, as well as using strong passwords and authentication measures.
Platform security refers to the measures taken to protect the underlying infrastructure of the cloud. This includes things like firewalls, intrusion detection systems, and malware protection.
Governance is all about establishing and enforcing policies and procedures for using the cloud.
This includes setting guidelines for who can access which data, creating incident response plans, and conducting audits to ensure compliance with regulations.
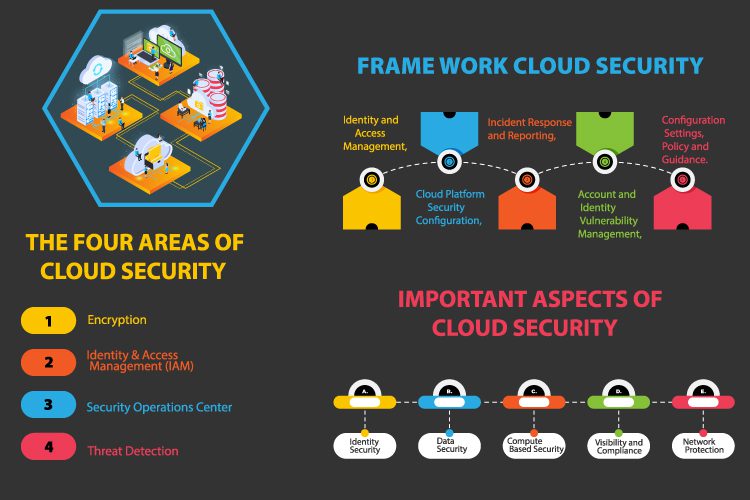
What are The Four Areas of Cloud Security?
The four areas are:
(1) Encryption, Identity & Access Management (IAM), Security Operations, and Threat Detection.
Cloud storage providers like Amazon Cloud Drive encrypt customer data with keys that are controlled solely by the user.
However, users may not realize their files are still accessible if the storage provider is hacked or legally compelled to provide access to customer data. Only end-to-end encrypted cloud storage should be used for sensitive data.
This way, only encrypted bits of data will ever touch third-party servers; it will first pass through client computers, so even if they’re hacked there are no unencrypted data to steal.
End-to-end encryption also allows users to share encrypted files with others via sharing links which can expire and be revoked at any time by anyone with the original encryption key.
(2) Cloud Service Providers (CSPs) can provide their customers with identity and access management services to help secure all their cloud applications, not just those that were developed in-house.
One of these identity providers may be an existing enterprise identity provider system typically used for on-premise systems.
However, CSPs are at risk due to multiple accounts created without consent by their users or employees creating them for convenience rather than security purposes.
Another common problem is when passwords are shared among several people within the organization leading to compromised credentials if one account is breached.
This type of security breach has historically been difficult for enterprises that already have trouble controlling access to sensitive data; it becomes even harder in the cloud where CSPs manage the infrastructure.
(3) Security operations centers (SOCs) are essential for identifying and responding to security threats in a timely manner.
They typically include analysts who are monitoring network traffic 24/7, looking for malicious or unauthorized activity. When a threat is identified, the SOC can take action to stop it.
However, many organizations find that setting up and running their own SOC is not feasible due to the cost and expertise required. In this case, it may be more advantageous to outsource this function to a third-party provider.
(4) Threat detection is another important security function that needs to be considered when moving to the cloud.
This includes both identifying new threats as they emerge and detecting ones that have already been successful in infiltrating an organization’s security.
Threat intelligence from a CSP is one option for organizations that lack the resources to implement their own threat detection methods.
Cloud providers can supply some or all of these capabilities depending on the needs of an individual organization and their willingness to invest in more advanced security features.
In any case, it is important that an organization understand what these various levels of protection offer and determine which ones they need for each application going into the cloud.
By taking this approach, they can be assured that their data is safe and compliant with industry regulations.
What is a Cloud Security Framework?
The NIST Cloud Security (CSF) is a framework that sets out six key categories for organizations to follow when conducting cloud security:
- Identity and Access Management,
- Cloud Platform Security Configuration,
- Incident Response and Reporting,
- Account and Identity Vulnerability Management,
- Configuration Settings, Policy and Guidance.
In order to comply with the CSF, an organization must have strong security measures in place across all six categories.
In some cases, these measures may be split between the customer and the provider while in other cases they will be under the total control of one party or another.
For example, while you may have strong identity management policies in place to protect access to your network infrastructure from unauthorized users, it may be the responsibility of the cloud provider to enforce similar policies for accessing the cloud infrastructure.
The CSF provides a comprehensive set of guidelines that organizations can use to ensure that their data is safe and secure when stored in the cloud.
It is important to note that the CSF is not a law or regulation, but rather a framework that can be used to help organizations comply with various regulations.
What is Cloud Security Architecture?
Cloud security architecture is the design and implementation of security measures for cloud infrastructure. It includes the security controls that are put in place to protect the cloud environment from unauthorized access and theft of data.
In addition, it also includes the policies and procedures that are put in place to ensure that the organization complies with regulations.
The cloud security architecture is generally split into three distinct layers:
The infrastructure layer covers the physical components of the cloud that are used to store customer data, such as servers and storage systems. It also includes firewalls, intrusion detection systems, and other network controls.
The platform layer covers the operating system (OS) and programming environment for applications running on the cloud.
The application layer is where customer-specific data and processing is performed.
While each of these layers requires different types of security measures, all three need to be properly managed in order to ensure that all customer data is secure.
Which Aspect is The Most Important For Cloud Security?
The most important aspects of cloud security are
- Identity Security
- Data Security
- Computer Based Security
- Visibility and Compliance
- Network Protection
While all five of these aspects are important, data security is the most critical. After all, if your data is stolen or compromised, it can be very difficult to recover it.
That’s why it’s important to use strong encryption methods and to keep your passwords and authentication credentials safe and secure.
What are Some Best Practices For Cloud Security?
There are a number of best practices you can follow to improve your cloud security posture:
- Use strong passwords and authentication measures.
- Encrypt your data when sending it to and from the cloud.
- Establish governance policies and procedures.
- Ensure that your cloud provider has adequate security measures in place.
- Regularly audit your cloud infrastructure for compliance with regulations.
- Stay up-to-date on the latest security threats and vulnerabilities.
Which are The Three Steps To Cloud Security?
Cloud security compliance
The Cloud Security Alliance (CSA) provides a comprehensive list of best practices that organizations can use to ensure that their data is secure when stored in the cloud.
For example, while some cloud providers may be responsible for securing the infrastructure layer, this does not mean that they will be responsible for securing customer-specific applications and data at rest on the platform and application layers.
In addition, it also means that they may not be responsible for protecting your critical and sensitive information and documents from unauthorized access or theft through shared public folders.
As such, it is important to understand which cloud providers are responsible for specific areas of security so you can choose one that meets all your requirements.
A key aspect of ensuring compliance with industry regulations is to have detailed security policies in place.
For example, the Payment Card Industry Data Security Standards (PCI DSS) requires organizations to encrypt all cardholder data at rest and in transit on any system that supports cardholder data.
Cloud Application Security
There are numerous applications being offered by cloud providers today. These cover a wide range of business areas including CRM, file sharing, messaging, customer support, billing and accounting, inventory control and many more.
While each of these applications has different requirements for privacy policies, they are commonly managed through API calls or web-based portals that must adhere to strict security controls.
This includes authentication measures such as password strength and multi-factor authentication; encryption technologies such as SSL/TLS; and regular change password policies.
Building secure applications in the cloud means understanding how these issues are addressed by various cloud providers.
For example, while traditional SSL certificates can be created to secure web-based portals, this may not be sufficient for many mobile applications that use APIs and need to encrypt data before transmitting it over wireless networks.
Understanding which encryption technologies your cloud provider supports is also important since some do not support older TLS protocols that have known vulnerabilities that hackers use to gain access to systems.
It is recommended that organizations implement an application security solution into their environment (e.g., Cloud Access Security Broker) so they can monitor all API calls across the distributed enterprise infrastructure.
Identifying Cloud Threats
Not surprisingly, there are several different ways that hackers can gain access to cloud-based systems and data.
One common way is through phishing attacks in which unsuspecting users are tricked into opening malicious email attachments or clicking on links to websites that contain malware. Another common method is by exploiting vulnerabilities in web applications.
Once inside a company’s network, hackers can often move laterally to other systems, including those in the cloud, using stolen credentials. This was recently demonstrated by the attack on Target that resulted in the theft of millions of credit card numbers.
To combat these threats, organizations need to have a comprehensive security strategy that includes regular vulnerability assessments and penetration testing of both their on-premises systems and those in the cloud.
In, they need to have threat intelligence capabilities in place so they can quickly identify and respond to new threats.
Organizations considering the cloud should carefully evaluate which areas of security are most important to them and then work with a cloud provider that can address those needs.
By doing so, they can be assured that their data is safe and compliant with industry regulations.
What Does Cloud Security Include?
Cloud security includes the technologies and processes that perform three key functions:
1) ensuring privacy,
2) preventing disclosure of business information, and
3) maintaining data quality.
The American Union’s GDPR regulation states in Article 32(b) “Personal data must be secure,” a term which the guidelines interpret as the ability to protect data from accidental or unauthorized access, destruction, alteration, or unauthorized use.
In order to achieve this, many cloud providers rely on a number of security technologies and processes such as firewalls, intrusion detection/prevention systems (IDS/IPS), encryption, tokenization, and data loss prevention (DLP).
They also deploy personnel who are responsible for implementing and managing these technologies, as well as for developing and enforcing the organization’s security policies.
Organizations need to understand which of these technologies and processes their cloud provider uses and how they work together to protect data.
They should also ensure that the provider has a robust security program that meets or exceeds their own security requirements.
What is Cloud Security Controls?
Cloud security controls are the technologies and processes that a cloud provider uses to protect data.
A cloud provider’s security controls should meet or exceed the organization’s own security requirements. They should also understand how these controls work together to protect data.
This includes knowing which technologies the provider uses, how they work together, and what their security policies are.
What is The Core Goal of Cloud Security?
Cloud security’s core goal is to protect the privacy of data. It does this by preventing unauthorized access, disclosure, and modification of data in transit and at rest.
Privacy laws such as HIPAA, GLBA, FISMA, PCI DSS, and PIPEDA restrict the degree to which an entity can share or store personally identifiable information (PII).
Cloud providers offer an attractive alternative to storing and processing data on-premises because they typically offer a more secure environment.
Who is Responsible For Cloud Security?
Cloud security is ultimately the responsibility of an organization’s board of directors, CEO, CIO/CTO, CISO, and other key executives.
However, in order to fully understand their cloud environment and how it meets compliance requirements, organizations need to engage their IT department as well.
IT must ensure that there aren’t any gaps between the controls a provider offers and those required by regulations such as HIPAA and GDPR.
This requires having an accurate understanding of what data resides where — whether on- or off-premises — and who has access to it.
How Can an Organization Evaluate a Cloud Provider’s Security?
When considering a new cloud provider or reviewing its offering for possible updates, organizations should carefully evaluate the provider’s security.
This includes understanding the technologies and processes the provider uses as well as their security policies.
They should also ensure that the provider has a robust security program that meets or exceeds their own security requirements.
An organization can evaluate a cloud provider’s security by understanding the technologies and processes they use, their security policies, and whether their security program meets or exceeds their own security requirements.
Now that you understand what cloud security is and how it works, you’re better prepared to make an informed decision about which cloud provider is right for your business needs.
By choosing a provider that uses robust security controls and meets or exceeds your own security requirements, you can be confident that your data is safe and secure.
As businesses move more of their operations to the cloud, the need for robust cloud security grows.
What are The Advantages of Cloud Security?
The cloud provides many advantages over using physical devices such as servers and storage, but those come with new security challenges.
Organizations can use the cloud to reduce costs, increase agility, and improve their business processes.
However, they need comprehensive cloud security to achieve these goals. This requires a holistic approach that addresses all aspects of organizational and service risk.
The cloud can improve security in several ways:
It allows organizations to securely access and shares their data from anywhere There is no worry about hardware failure or unplanned downtime due to natural disasters or other events.
It reduces the costs associated with managing and securing on-premises resources Using a multi-cloud environment provides protection against threats and outages in a single cloud If an endpoint device gets compromised.
It doesn’t affect other devices because all of an organization’s data isn’t stored on one physical server Organizations have more control over key/application management processes In addition to these advantages, there are 3 primary motivations for using the cloud:
A desire for greater agility Faster innovation Improved business process efficiency Cloud security plays a critical role in helping protect data and achieve these 3 motivations.
Where is Cloud Security Used?
Cloud security is used in a variety of settings, including:
Public clouds Private clouds Hybrid clouds Community clouds Cloud security is also being used in new ways, such as with the Internet of Things (IoT) and other edge computing devices.
As more and more devices are connected to the internet, the need for robust cloud security increases. Cloud services provide many advantages over using physical devices, but those come with new security challenges.
Organizations can use the cloud to reduce costs, increase agility, and improve their business processes.
However, they need comprehensive cloud security to achieve these goals. This requires a holistic approach that addresses all aspects of organizational and service risk.
What are Cloud Security Threats?
New threats are being introduced daily and existing threats continue to evolve, which makes it challenging for cloud service providers (CSPs) and their customers to stay ahead of the threat landscape.
This is particularly true with increased usage of DevOps and agile development techniques because traditional security practices and processes can fall short in these environments.
Common cloud security threats include:
Data breaches System availability loss Denial of service (DoS) attacks Data tampering Unauthorized access Physical infrastructure insecurity.
Threats are amplified because many organizations are moving sensitive data to the cloud, where they have longer retention periods.
This means that compromises can be more damaging when it comes time to mitigate them.
In addition, CSPs do not own or control everything on a customer’s system. Customers must share the responsibility of mitigations and be diligent about mitigating threats on their side as well.
What Technology Factors are Responsible For Cloud Security Problems?
There are several technical factors that contribute to cloud security problems:
IaaS and PaaS can make it difficult to control access to resources and data Microservices architectures can make it difficult to track and secure data flows.
Shared services can increase the attack surface area. Security misconfiguration is a common issue with cloud deployments.
Automation can create security gaps if not done properly Lack of visibility can make it difficult to identify and respond to threats.
These factors create a complex environment in which organizations need to take a holistic approach to cloud security in order to protect their data and systems.
What are CCM and CAIQ?
Cloud security is a complex and constantly evolving field. To help organizations manage the risk associated with using cloud services, ISO/IEC created two new standards:
Cloud Control Matrix (CCM) provides a framework for assessing and managing the security risks of cloud services
ISO/IEC 27001:2013 contains guidance for implementing an information security management system (ISMS) that can be used to manage the security risks of cloud services
Cloud Assurance and Intelligence Quick View (CAIQ) is a tool that provides an overview of the security posture of a cloud service provider (CSP) and enables CSPs to self-assess their security posture
Together, these standards can help organizations manage the security risks associated with using cloud services.
Best Cloud Security Certifications to consider in 2024
1. (ISC)² Certified Cloud Security Professional – CCSP
The CISSP is one of the most valuable cloud security certifications in the market because of its value. You must pass a certification examination to earn this credential.
It verifies that you have up-to-date technical understanding and that you manage, design, and secure data as well as applications and infrastructure in the cloud.
You must follow the best practices as defined by cybersecurity professionals, including policies and strategies, to gain this certificate.
The AWS Certified Solutions Architect – Certified Cloud Solutions Professional (ECSSP) certification is for computer scientists employed in the field of cloud computing who work as security consultants, enterprise architects, systems engineers, security administrators, and security engineers.
This is one of the most difficult and up-to-date cybersecurity certifications on the market with a high price tag!
2. Professional Cloud Security Engineer by Google
The Associate-level certification in Cloud Security validates your skills in cloud security configuration, data protection, compliance, and network security setup.
It also covers access management within a cloud solution environment and management of operation within the cloud.
A cloud security expert must understand all aspects of cloud security, which include managing identity and access management (IAM), data protection via technologies, and incident response.
The credential demands 3 or more years of expertise in the field and 1 or more years of experience designing and managing solutions with GCP.
3. GIAC Cloud Security Automation – GCSA
The GCBA covers the latest DevSecOps strategies that are used to create, design and deploy systems and apps successfully.
This test validates not only that your cloud security automation theory is solid, but also that you can apply the DevSecOps principles in an automated fashion.
Anyone working in a public cloud, DevOps, systems administrators, security analysts, and engineers should take this exam.
There are numerous topics addressed in the coursework, including continuous integration, continuous delivery, automated configuration management, continual monitoring, and someone who works with open-source tools such as the AWS toolchain or Azure services.
4. CompTIA Cloud+
CompTIA Cloud+ validates the abilities and knowledge you’ll need to operate, design, and maintain cloud infrastructure services.
Aviator seeks candidates with at least two years of experience in system administration, preferably 2 to 3 Cloud+ certification is required for a variety of occupations, including cloud specialists, network engineers, network administrators, system administrators, cloud engineers, cloud developers, and product managers in the cloud.
Management, maintenance, verification, security monitoring and configuration (including troubleshooting) are the skills needed for this certification.
5. Certificate of Cloud Security Knowledge – CCSK
The Cloud Security Alliance’s CCSK certification is for cloud-savvy professionals and is widely recognized as a standard of competence and practical experience in cloud security.
To demonstrate their abilities to practically apply controls particularly suited for the cloud, professionals in information security jobs, managers, consultants, and security architects should acquire this certificate.
The test is open-book and can be studied either on your own or through a comprehensive course.
Final Words
In conclusion, as more and more of our lives move online it is important to understand the risks that come with these digital assets.
Cloud security can help you stay protected from cyber threats by teaching you what a threat actor looks like, how they operate on your network and some basic best practices for staying safe in a cloud environment.
The next time someone asks about cybersecurity or if their company needs it – go ahead and send them here!



