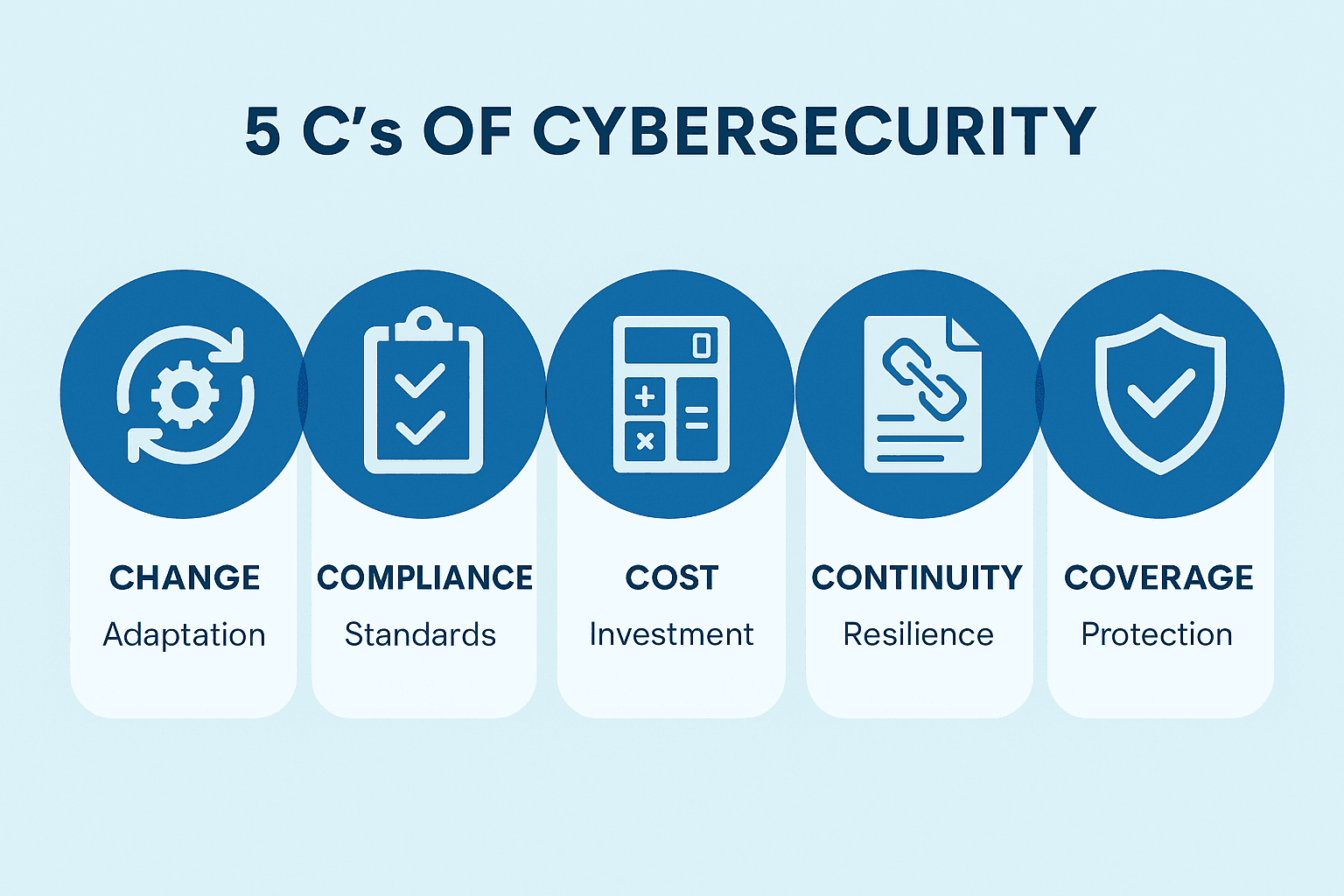
The Importance of Cybersecurity in the United States: Detailed Guide
In an era where digital infrastructure underpins nearly every facet of American life from national defense and healthcare to banking and transportation, cybersecurity has become a cornerstone of national security…